Back to Courses







Computer Science Courses - Page 191
Showing results 1901-1910 of 2309

Introduction to Cyber Attacks
This course provides learners with a baseline understanding of common cyber security threats, vulnerabilities, and risks. An overview of how basic cyber attacks are constructed and applied to real systems is also included. Examples include simple Unix kernel hacks, Internet worms, and Trojan horses in software utilities. Network attacks such as distributed denial of service (DDOS) and botnet- attacks are also described and illustrated using real examples from the past couple of decades.
Familiar analytic models are outlined such as the confidentiality/integrity/availability (CIA) security threat framework, and examples are used to illustrate how these different types of threats can degrade real assets. The course also includes an introduction to basic cyber security risk analysis, with an overview of how threat-asset matrices can be used to prioritize risk decisions. Threats, vulnerabilities, and attacks are examined and mapped in the context of system security engineering methodologies.

Security Features and Advanced Threat Prevention
In this course, we will describe security services such as Intrusion Prevention System (IPS), user-based firewalls, and how they are configured. You will be introduced to Juniper’s security features, such as antivirus, antispam, content filtering, and Web filtering, along with their functionality and usage. Juniper ATP Cloud (Juniper’s cloud-based Advanced Threat Prevention (ATP) service) will be introduced, along with its features, implementation, and monitoring. The course will also explain a very important feature of firewall security—Network Address Translation (NAT).

Create professional mockups on Moqups
During this project, you will be able to discover Moqups, a website that will allow you to create professional mockups, quickly and easily. You will be able to create various mockups for any type of professional project, which will allow you to visualize your information.
This project is intended for people and professionals wishing to visualize data through mockups, diagrams, prototypes of all kinds.

Creating a Looker Modeled Query and Working with Quick Start
This is a self-paced lab that takes place in the Google Cloud console.
Looker provides the ability for LookML developers to build modeled queries that help all Looker business users quickly get started and easily explore data in the platform.
This three-task lab will provide you with practical, hands-on experience using the query parameter to create a modeled query for an Explore. The modeled query is listed in the Quick Start section of a blank Explore. Modeled queries are extremely helpful to Looker business users, since you can specify elements like the dimensions, measures, filters, and pivots that may be the most relevant and insightful. In this lab you will learn how to create a modeled query, which can be a helpful starting point for users who are new to Looker and learning how to query data.

Functional Programming in Scala Capstone
In the final capstone project you will apply the skills you learned by building a large data-intensive application using real-world data.
You will implement a complete application processing several gigabytes of data. This application will show interactive visualizations of the evolution of temperatures over time all over the world.
The development of such an application will involve:
— transforming data provided by weather stations into meaningful information like, for instance, the average temperature of each point of the globe over the last ten years ;
— then, making images from this information by using spatial and linear interpolation techniques ;
— finally, implementing how the user interface will react to users’ actions.

Esports Management Capstone Project
We will analyze the pros and cons of creating a single or multiple Esport organization and recommend an effective branding strategy for a hypothetical Esport organization based on current Esport branding considerations.
You will develop a plan for recruiting funding resources for a hypothetical Esports organization and choose an Esport organization role of interest, other than Owner, and describe your reasoning.

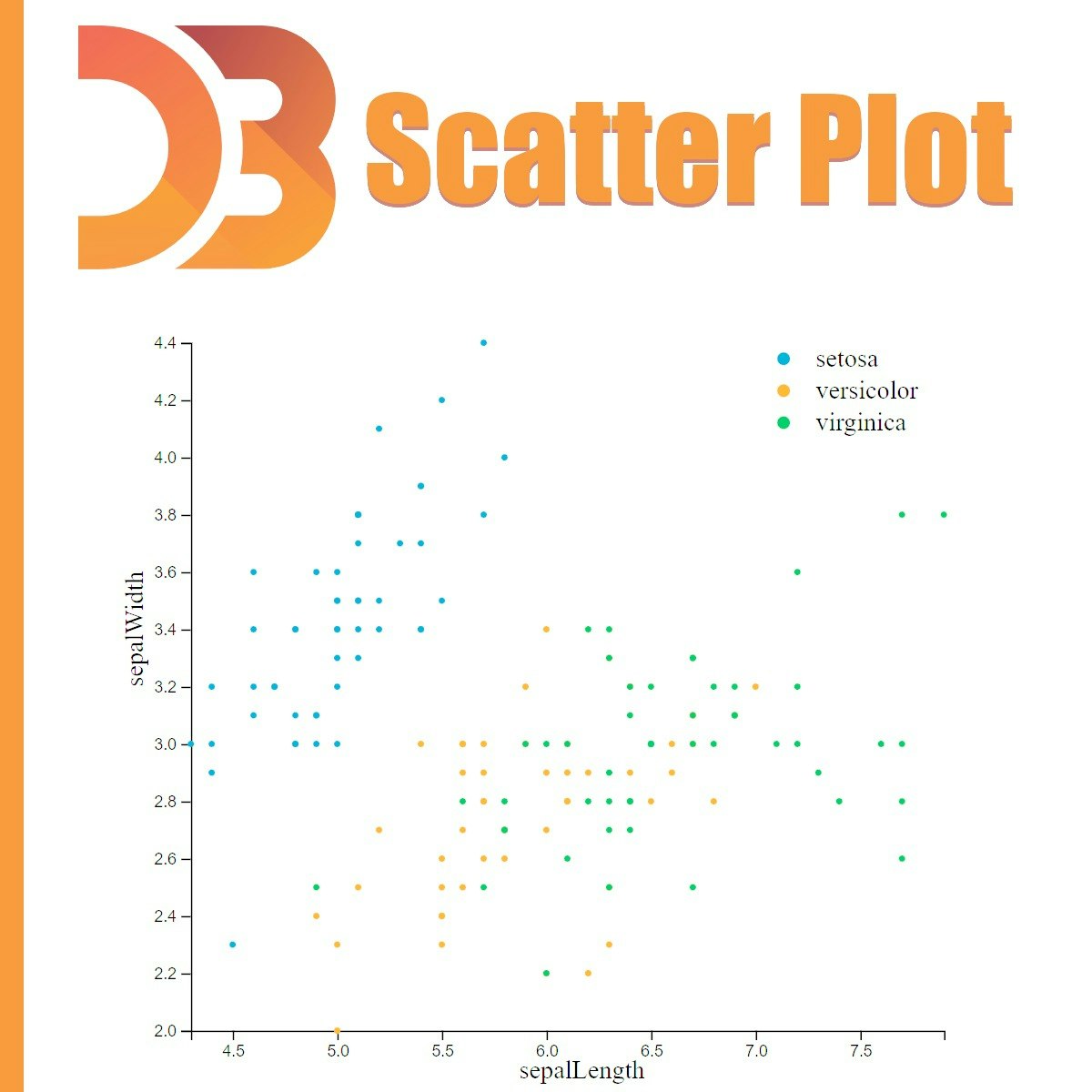
A Simple Scatter Plot using D3 js
During this guided project, you will create a simple scatter plot using D3 js. Starting from loading our dataset we are going to cover some steps in order to create a fully functional scatter plot. We will also cover some important topics in data visualization such as Linear and Ordinal scaling to best visualize our data. Having the knowledge of javascript programming language and the basics of d3 js are the two most important prerequisites to get the most out of this guided project.

Programming Reactive Systems (Scala 2 version)
Reactive programming is a set of techniques for implementing scalable, resilient and responsive systems as per the Reactive Manifesto. Such systems are based on asynchronous message-passing, and their basic building-blocks are event handlers. This course teaches how to implement reactive systems in Scala and Akka by using high-level abstractions, such as actors, asynchronous computations, and reactive streams.
You will learn how to:
- use, transform and sequence asynchronous computations using Future values
- write concurrent reactive systems based on Actors and message passing, using untyped Akka and Akka Typed
- design systems resilient to failures
- implement systems that can scale out according to a varying workload
- transform and consume infinite and intermittent streams of data with Akka Stream in a non-blocking way
- understand how back-pressure controls flows of data

Capstone: Retrieving, Processing, and Visualizing Data with Python
In the capstone, students will build a series of applications to retrieve, process and visualize data using Python. The projects will involve all the elements of the specialization. In the first part of the capstone, students will do some visualizations to become familiar with the technologies in use and then will pursue their own project to visualize some other data that they have or can find. Chapters 15 and 16 from the book “Python for Everybody” will serve as the backbone for the capstone. This course covers Python 3.

Introduction to Blockchain for Global Commerce
This course discusses the limitations of the Internet for business and economic activity and explains how blockchain technology represents the way forward. After completing this course, you will be able to explain what blockchain is, how it works, and why it is revolutionary. You will learn key concepts such as mining, hashing, proof-of-work, public key cryptography, and the double-spend problem. You’ll be able to describe seven design principles for blockchain technology, and the challenges facing the people developing it. By the end of this course, you’ll learn how and why transacting on the blockchain can help us bring about a future that is faster, fairer, and more distributed than the world we inhabit today.
