Back to Courses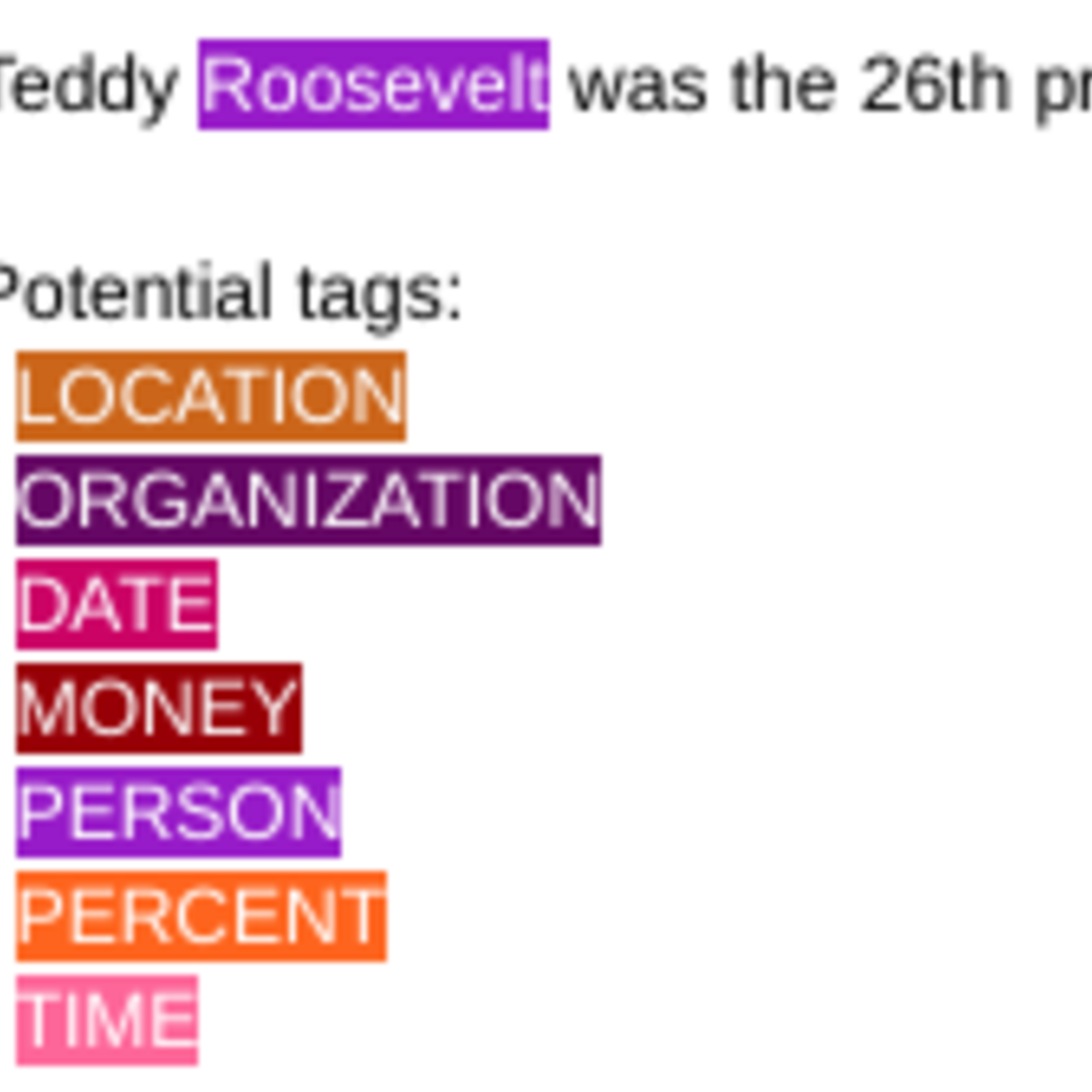









Algorithms Courses - Page 4
Showing results 31-40 of 326

Named Entity Recognition using LSTMs with Keras
In this 1-hour long project-based course, you will use the Keras API with TensorFlow as its backend to build and train a bidirectional LSTM neural network model to recognize named entities in text data. Named entity recognition models can be used to identify mentions of people, locations, organizations, etc. Named entity recognition is not only a standalone tool for information extraction, but it also an invaluable preprocessing step for many downstream natural language processing applications like machine translation, question answering, and text summarization.
This course runs on Coursera's hands-on project platform called Rhyme. On Rhyme, you do projects in a hands-on manner in your browser. You will get instant access to pre-configured cloud desktops containing all of the software and data you need for the project. Everything is already set up directly in your internet browser so you can just focus on learning. For this project, you’ll get instant access to a cloud desktop with Python, Jupyter, and Keras pre-installed.
Notes:
- You will be able to access the cloud desktop 5 times. However, you will be able to access instructions videos as many times as you want.
- This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Number Theory and Cryptography
A prominent expert in the number theory Godfrey Hardy described it in the beginning of 20th century as one of the most obviously useless branches of Pure Mathematics”. Just 30 years after his death, an algorithm for encryption of secret messages was developed using achievements of number theory. It was called RSA after the names of its authors, and its implementation is probably the most frequently used computer program in the world nowadays. Without it, nobody would be able to make secure payments over the internet, or even log in securely to e-mail and other personal services. In this course we will start with the basics of the number theory and get to cryptographic protocols based on it. By the end, you will be able to apply the basics of the number theory to encrypt and decrypt messages, and to break the code if one applies RSA carelessly. You will even pass a cryptographic quest!
As prerequisites we assume only basic math (e.g., we expect you to know what is a square or how to add fractions), basic programming in python (functions, loops, recursion), common sense and curiosity. Our intended audience are all people that work or plan to work in IT, starting from motivated high school students.

Improving Deep Neural Networks: Hyperparameter Tuning, Regularization and Optimization
In the second course of the Deep Learning Specialization, you will open the deep learning black box to understand the processes that drive performance and generate good results systematically.
By the end, you will learn the best practices to train and develop test sets and analyze bias/variance for building deep learning applications; be able to use standard neural network techniques such as initialization, L2 and dropout regularization, hyperparameter tuning, batch normalization, and gradient checking; implement and apply a variety of optimization algorithms, such as mini-batch gradient descent, Momentum, RMSprop and Adam, and check for their convergence; and implement a neural network in TensorFlow.
The Deep Learning Specialization is our foundational program that will help you understand the capabilities, challenges, and consequences of deep learning and prepare you to participate in the development of leading-edge AI technology. It provides a pathway for you to gain the knowledge and skills to apply machine learning to your work, level up your technical career, and take the definitive step in the world of AI.

Algorithmic Thinking (Part 2)
Experienced Computer Scientists analyze and solve computational problems at a level of abstraction that is beyond that of any particular programming language. This two-part class is designed to train students in the mathematical concepts and process of "Algorithmic Thinking", allowing them to build simpler, more efficient solutions to computational problems.
In part 2 of this course, we will study advanced algorithmic techniques such as divide-and-conquer and dynamic programming. As the central part of the course, students will implement several algorithms in Python that incorporate these techniques and then use these algorithms to analyze two large real-world data sets. The main focus of these tasks is to understand interaction between the algorithms and the structure of the data sets being analyzed by these algorithms.
Once students have completed this class, they will have both the mathematical and programming skills to analyze, design, and program solutions to a wide range of computational problems. While this class will use Python as its vehicle of choice to practice Algorithmic Thinking, the concepts that you will learn in this class transcend any particular programming language.

C Programming: Using Linux Tools and Libraries - 7
Learn how to use professional tools and libraries to write and build C programs within the Linux operating system.
This seventh and final course in the C Programming with Linux Specialization will allow you to develop and use your C code within the Linux operating system. Using libraries in C is a fundamental concept when it comes to sharing code with others. In addition to compiling and linking, you will also learn how to pass arguments to an executable program.
As you embark on your future career as a programmer, you will be able to continue your coding adventures with professional coding environments used by C programmers around the world.
Why learn C and not another programming language? Did you know that smartphones, your car’s navigation system, robots, drones, trains, and almost all electronic devices have some C-code running under the hood? C is used in any circumstance where speed and flexibility are important, such as in embedded systems or high-performance computing.
At the end of this course, you will reach the last milestone in the C Programming with Linux Specialization, unlocking the door to a career in computer engineering.
Your job Outlook:
- Programmers, developers, engineers, managers, and related industries within scientific computing and data science;
- Embedded systems such as transportation, utility networks, and aerospace;
- Robotics industry and manufacturing;
- IoT (Internet of Things) used in smart homes, automation, and wearables.
- IEEE, the world’s largest technical professional organization for the advancement of technology, ranks C as third of the top programming languages of 2021 in demand by employers. (Source: IEEE Spectrum)
This course has received financial support from the Patrick & Lina Drahi Foundation.

OpenVINO Beginner: Building a Crossroad AI Camera
In this 2-hour long project-based course, you will learn how to Build a Crossroad AI Camera:
Learning Objective 1: By the end of Task 1, you will be able to explain the OpenVINO™ Toolkit Workflow and OpenVINO™ Toolkit Components
Learning Objective 2: By the end of Task 2, you will be able to operationalize models using the Model Downloader utility
Learning Objective 3: By the end of Task 3, you will be able to perform Model Preparation, Conversion and Optimization
Learning Objective 4: By the end of Task 4, you will be able to Running and Tuning Inference
Learning Objective 5: By the end of Task 5, you will be able to create visualization of Person Attributes and Person Re-identification (REID) information for each detected person in an Image/Video/Camera input.

Build a Word Jumble using Java Basics
By the end of this project, you will create a word jumble game using Java Swing. This project will give you a great head start towards learning more and mastering one of the most used programming languages in the world. In this project you will learn many basic fundamentals such as data structures, variables, loops etc. Learning and understanding Java Swing will help you progress in the programming field by creating simple Java applications.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Using BigQuery in the Google Cloud Console
This is a self-paced lab that takes place in the Google Cloud console.
This lab shows you how to query public tables and load sample data into BigQuery using the GCP Console. Watch the following short video Get Meaningful Insights with Google BigQuery.

Mathematical Foundations for Cryptography
Welcome to Course 2 of Introduction to Applied Cryptography. In this course, you will be introduced to basic mathematical principles and functions that form the foundation for cryptographic and cryptanalysis methods. These principles and functions will be helpful in understanding symmetric and asymmetric cryptographic methods examined in Course 3 and Course 4. These topics should prove especially useful to you if you are new to cybersecurity. It is recommended that you have a basic knowledge of computer science and basic math skills such as algebra and probability.

Creating a Rock, Paper, Scissors Game in Python
By the end of this project, you will be able to create a simple interactive game of rock, paper, or scissors. Throughout this guided project, you will be introduced to the basic skills needed for every programming language such as different data types, loops, and if conditions. Each part of the project will prepare you to code on your own in Python language, whether to create a game or simple coding.
Python programming is one of the easiest programming languages since its syntax is English-like. It is used in many applications and mastering it will definitely pave a way for you to start a career in any programming-based field. Python is also the base for the machine learning and deep learning field.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.
Popular Internships and Jobs by Categories
Find Jobs & Internships
Browse
© 2024 BoostGrad | All rights reserved