Back to Courses








Computer Science Courses - Page 50
Showing results 491-500 of 2309

Agile Projects: Creating User Stories with Value in Taiga
This guided project was developed to engage and harness your visionary and exploratory abilities. During this course, you will use input from previous phases of project development. Together we will identify, map, and analyse User Stories which are the components that make up the themes of the customer experience with the product and service.
This is an important step for individuals or companies wanting to map value for customer to product features in new products or services; also, for enhancing their existing offerings. By the end of this guided project, you will be fluent in identifying and creating User Stories for agile projects.
We will discuss directions for the next phase of the project development; furthermore, the learned concepts and tools will help you generate solutions for use as part of your project management solutions and in presentations to various stakeholders.

Check Point Jump Start - CloudGuard Workload Protection
The purpose of this program is to give you an insight into the security challenges involving workload protection and application security in the cloud, and Check Point’s solutions for those challenges. The program will also enable you to perform a basic deployment and configuration of the various solutions under the CloudGuard umbrella.
Chapter 1 - Program introduction
Chapter 2 – Introduction to Workload protection and application security
Lesson 1: Introduction to cybersecurity in the cloud
Lesson 2: Security challenges of cloud workloads
Lesson 3: CloudGuard Workload Protection
Chapter 3 - CloudGuard Workload Protection - Container Security
Lesson 1: Recap
Lesson 2: Runtime Protection
Lesson 3: Image Assurance
Lesson 4: Admission Control
Lesson 5: Threat Intelligence
Lesson 6: Posture Management
Lesson 7: Deployment
Lesson 8: Deployment troubleshooting
Chapter 4 - Shifting protection to the left with CloudGuard ShiftLeft
Lesson 1: Introduction to shifting security to the left
Lesson 2: Deployment
Chapter 5 – CloudGuard Workload protection - Serverless Security
Lesson 1: Serverless security
Lesson 2: CloudGuard Serverless Security for AWS Lambda
Lesson 3: Deployment
Chapter 6 – CloudGuard Application Security and API Protection
Lesson 1: Introduction to application security and API protection
Lesson 2: The CloudGuard AppSec solution
Lesson 3: Architecture and deployment considerations
Lesson 4: Deployment process
Lesson 5: Deployment
Lesson 6: Setting up API protection
Lesson 7: Data and customization of AppSec policy
Chapter 7 – Program summary
Check Point CloudGuard provides unified cloud-native security for all your assets and workloads, giving you the confidence to automate security, prevent threats, and manage posture – everywhere – across your multi-cloud environment.

TypeScript String Properties and Methods
This project will teach you TypeScript string properties and methods in the TypeScript playground which will make string handling easier.Since text data is commonly used as a “string” in TypeScript, the ability to use and manipulate strings is a core component of TypeScript programming. So in this guided project you are going to learn different string properties and methods which are important for string manipulation operations.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Align Design Teams with SCAMPER Brainstorming in Miro
By the end of this project, you will be able to use SCAMPER brainstorming strategies to enhance product and service development by efficiently moving your team to the improvement and innovation stages of user experience and user interface design.
To do this, you will gain hands-on experience applying SCAMPER brainstorming strategies and visualizing the results in the Miro online visual collaboration platform for teamwork.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Managing an Agile Team
While agile has become the de facto standard for managing digital innovation teams, many wonder if they’re doing it ‘right’. Twitter is full of jokes about how teams say they do agile but don’t ‘really’ do it. The reality is that getting the most out of agile is less about observing specific procedures and more about how a team focuses and measures their progress.
Rather than just boring you with an accounting of agile methodologies, this course focuses on helping you better charter your team’s focus, definition of success, and practice of agile. While learning about agile mainstays like Scrum, XP, and kanban, you’ll also learn to help your team ask the right questions about how they’re working and facilitate good answers on how agile can help.
This course is supported by the Batten Institute at UVA’s Darden School of Business. The Batten Institute’s mission is to improve the world through entrepreneurship and innovation: www.batteninstitute.org.

Introduction to Data Science in Python
This course will introduce the learner to the basics of the python programming environment, including fundamental python programming techniques such as lambdas, reading and manipulating csv files, and the numpy library. The course will introduce data manipulation and cleaning techniques using the popular python pandas data science library and introduce the abstraction of the Series and DataFrame as the central data structures for data analysis, along with tutorials on how to use functions such as groupby, merge, and pivot tables effectively. By the end of this course, students will be able to take tabular data, clean it, manipulate it, and run basic inferential statistical analyses.
This course should be taken before any of the other Applied Data Science with Python courses: Applied Plotting, Charting & Data Representation in Python, Applied Machine Learning in Python, Applied Text Mining in Python, Applied Social Network Analysis in Python.

Preparing for Your Associate Cloud Engineer Journey
This course helps you structure your preparation for the Associate Cloud Engineer exam. You will learn about the Google Cloud domains covered by the exam and how to create a study plan to improve your domain knowledge.

Cybersecurity Policy for Aviation and Internet Infrastructures
In this course we will examine the aviation and Internet infrastructures, and various policies that have been developed to help guide and strengthen their cybersecurity programs. The aviation and Internet infrastructures are also considered "lifeline infrastructure" as part of the transportation and communications sectors. Both subsectors are overseen by the Department of Homeland Security National Protection and Programs Directorate which manages the DHS National Infrastructure Protection Program. SSA responsibility for the aviation subsector is shared between the Transportation Security Administration and Federal Aviation Administration under the auspices of the Department of Homeland Security and Department of Transportation respectively. The Department of Homeland Security retains sole responsibility as the Sector-Specific Agency for the Internet subsector. While TSA and FAA have regulatory over the aviation subsector, DHS has no regulatory authority whatsoever over the Internet. In response to Executive Order 13636 issued by President Obama in February 2013, both sets of SSAs recommended continuing with voluntary cybersecurity measures. TSA and FAA reported they were working to implement the Transportation Roadmap across all transportation subsectors, including aviation. DHS reported that it was working with Internet providers to implement the Cyber Assessment Risk Management Approach. Despite some differences, the Transportation Roadmap and CARMA are very similar to the NIST Cybersecrity Framework and ES-C2M2 examined previously. That is to say, they are predicated on a continuous improvement process that engages the whole organization in identifying and implementing incremental changes to enhance cybersecurity practices based on prevailing standards. This module will examine both the aviation and Internet lifeline infrastructure subsectors, and elements and application of the Transportation Roadmap and CARMA.

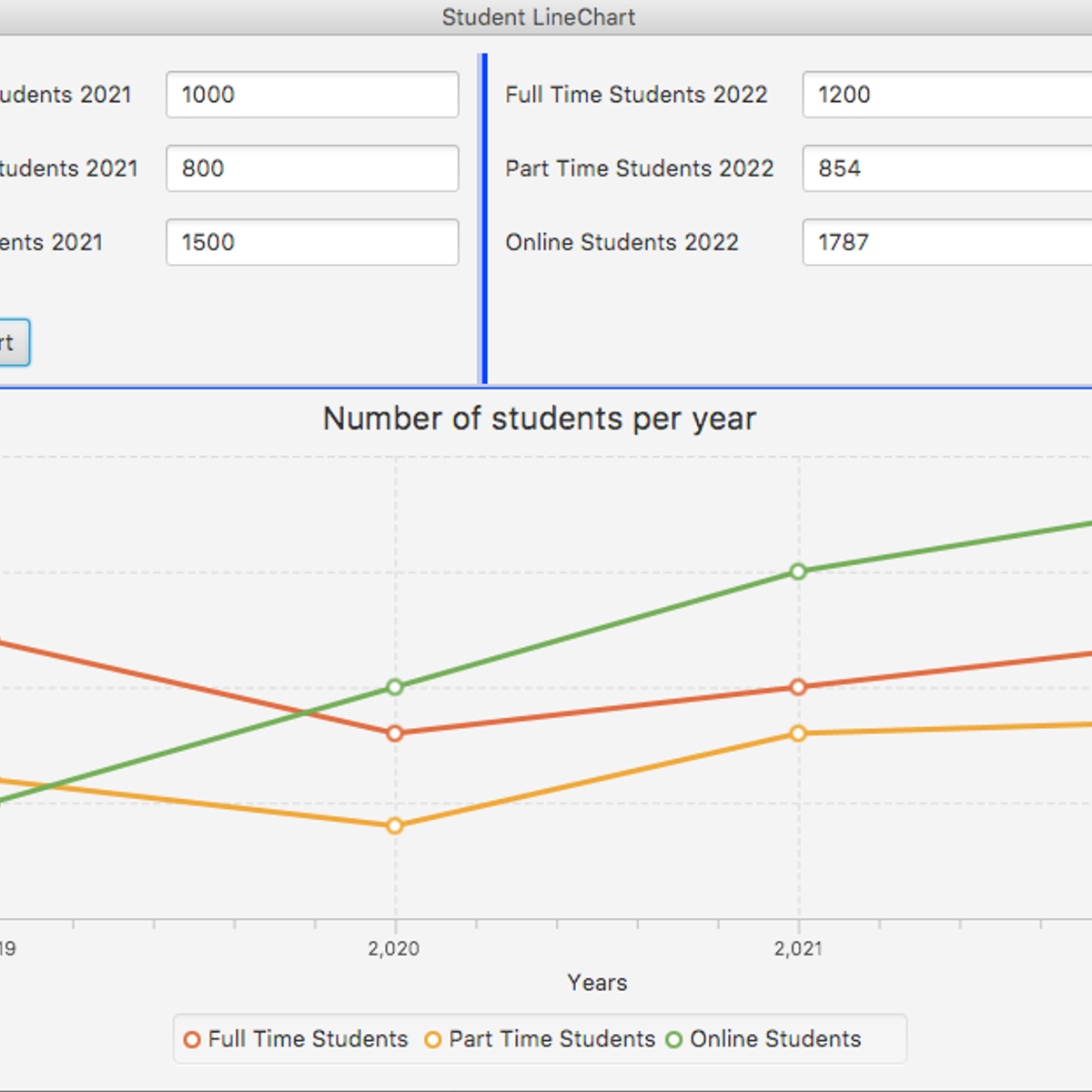
Display Student Data with Linechart and Separator in JavaFX
In this project, the learners will create a GUI that uses two separators to display controls and a line chart that shows the number of students who have enrolled part time, full time, and online. When data is entered in a set of text fields, a button is clicked to show a line chart for the number of students who have enrolled in these modes of study from 2019 to 2022.

Data Mining Methods
This course covers the core techniques used in data mining, including frequent pattern analysis, classification, clustering, outlier analysis, as well as mining complex data and research frontiers in the data mining field.
Data Mining Methods can be taken for academic credit as part of CU Boulder’s Master of Science in Data Science (MS-DS) degree offered on the Coursera platform. The MS-DS is an interdisciplinary degree that brings together faculty from CU Boulder’s departments of Applied Mathematics, Computer Science, Information Science, and others. With performance-based admissions and no application process, the MS-DS is ideal for individuals with a broad range of undergraduate education and/or professional experience in computer science, information science, mathematics, and statistics. Learn more about the MS-DS program at https://www.coursera.org/degrees/master-of-science-data-science-boulder.
Course logo image courtesy of Lachlan Cormie, available here on Unsplash: https://unsplash.com/photos/jbJp18srifE
