Back to Courses






Computer Science Courses - Page 119
Showing results 1181-1190 of 2309

3D, perspective text effect on Photoshop
By the end of this project, you will be able to create a 3D, perspective text effect using Adobe Photoshop.
Throughout the project, you will be able to use Adobe Photoshop with its different tools. You will be able to create a 3D and perspective text effect that you will use to create an architecture firm logo along with the landing page of their website.
You will be exposed to the Vanishing Point Filter as well as the 3D workspace on Photoshop.
This guided project is for intermediate graphic designers and intermediate digital designers who are interested in learning how to create a 3D and perspective text effect in Adobe Photoshop. Using the tools in Adobe Photoshop, an architecture firm logo along with the landing page of their website. By creating this, you will contribute to completing the branding of the architecture firm knowing that a logo is always one of the most important pillars of a successful branding and this project will help you achieve that.
Adobe Photoshop is a software that is extensively used for raster image editing, graphic design and digital art. It makes use of layering to allow for depth and flexibility in the design and editing process, as well as provide powerful tools that, when combined, are capable of just about anything.
It will be, undoubtedly, a great asset throughout your future career as a designer.

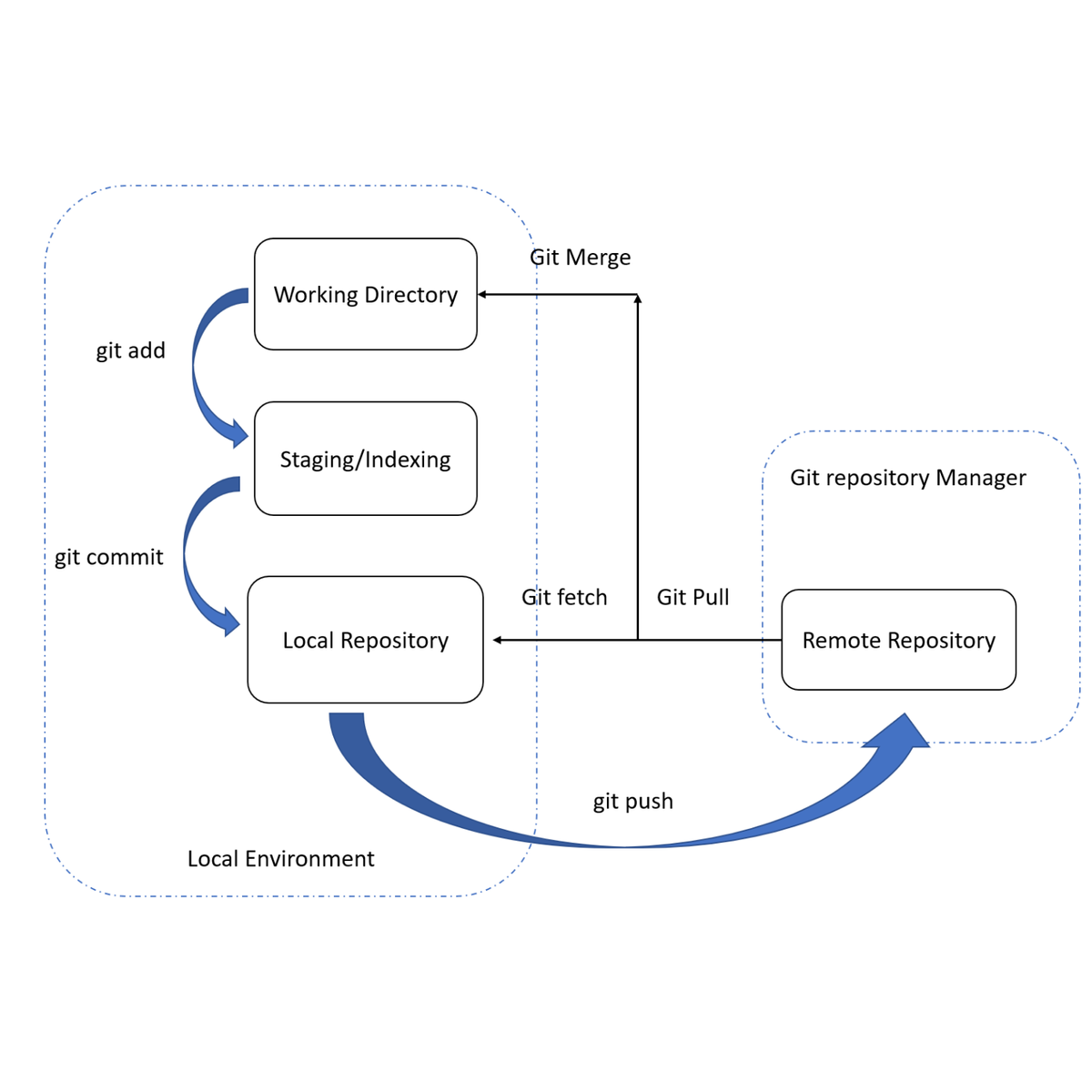
Source control management for test automation with Git
Every development team or automation team needs a good way to collaborate and manage changes and to version code in their codebase. That’s why they use source control or version control.
Source control refers to tracking and managing changes to code. This ensures that developers are always working on the right version of the source code.
Git is one of the most widely used open-source distributed source code management systems for tracking changes in source code during software development.
In this 1-hour long project-based course, you will learn how to
1. Execute GIT commands via Eclipse plugin and CLI
2. Clone, Fetch and Pull code from remote repository
3. Commit, merge and push code to the remote repository

Games, Sensors and Media
You will learn to make fluid digital interactive experiences that are suitable for gaming and use the advanced sensor hardware built into the iPhone and iPad. This includes drawing 2D graphics, playing sounds and music, integrating with Game Center, the iOS physics engine and detecting device orientation and location.
Upon completing this course, you will be able to:
1. Use the reverse geocode service to convert latitude and longitude to location names
2. Implement GeoFences to make an app efficiently monitor an iOS device’s location
3. Leverage the power of accelerometers, magnetometers and gyroscopes to orient a device in physical space
4. Create an app that responds to ambient light levels by using screen brightness as a proxy
5. Play sound effects and other media as audio
6. Make a game like Pong
7. Make a game like Breakout
8. Manipulate graphics in a game environment
9. Use the physics engine to create realistic game worlds
10. React to multi-touch events for complex interaction design
11. Detect and respond to collisions and contacts efficiently
12. Chain complex sequences of actions, animations and sounds with precision
13. Animate multi-frame sprites
14. Create particle systems to simulate fire, smoke and magic (and more!)
15. Interface with Game Center to create leaderboards and achievements that can be shared through social networks

Create UI in Unity Part 1 - Screen Overlay Canvas
In this 90-minute, project-based course, you will be introduced to Unity's User Interface (UI) Toolkit for building a Heads Up Display (HUD) for your game. This project covers creating and setting up each UI component and writing simple scripts that will update the UI for player-feedback.
The guided project will introduce you to the following Unity UI concepts:
- Canvas
- Rect Transform
- Text
- Image
- Animation
- Coding techniques including the Time Class, String Formatting, Inheritance and Polymorphism
This is Part 1 of a four-part series on creating a user interface for your game or other Unity application. Part 2 covers creating a world-space canvas, part 3 will demonstrate how to create a settings menu and part 4 will show you how to design the UI to automatically adapt to the aspect ratio of any screen.
This is a stand-alone guided project, and also serves as an optional but recommended foundation for the "User Interface" series.
This series makes use of the sci-fi-themed Unity project created in Create Power-Ups and Obstacles with C# in Unity. It compliments this guided project and, although not a prerequisite, is recommended for a more well-rounded understanding of the concepts presented herein.

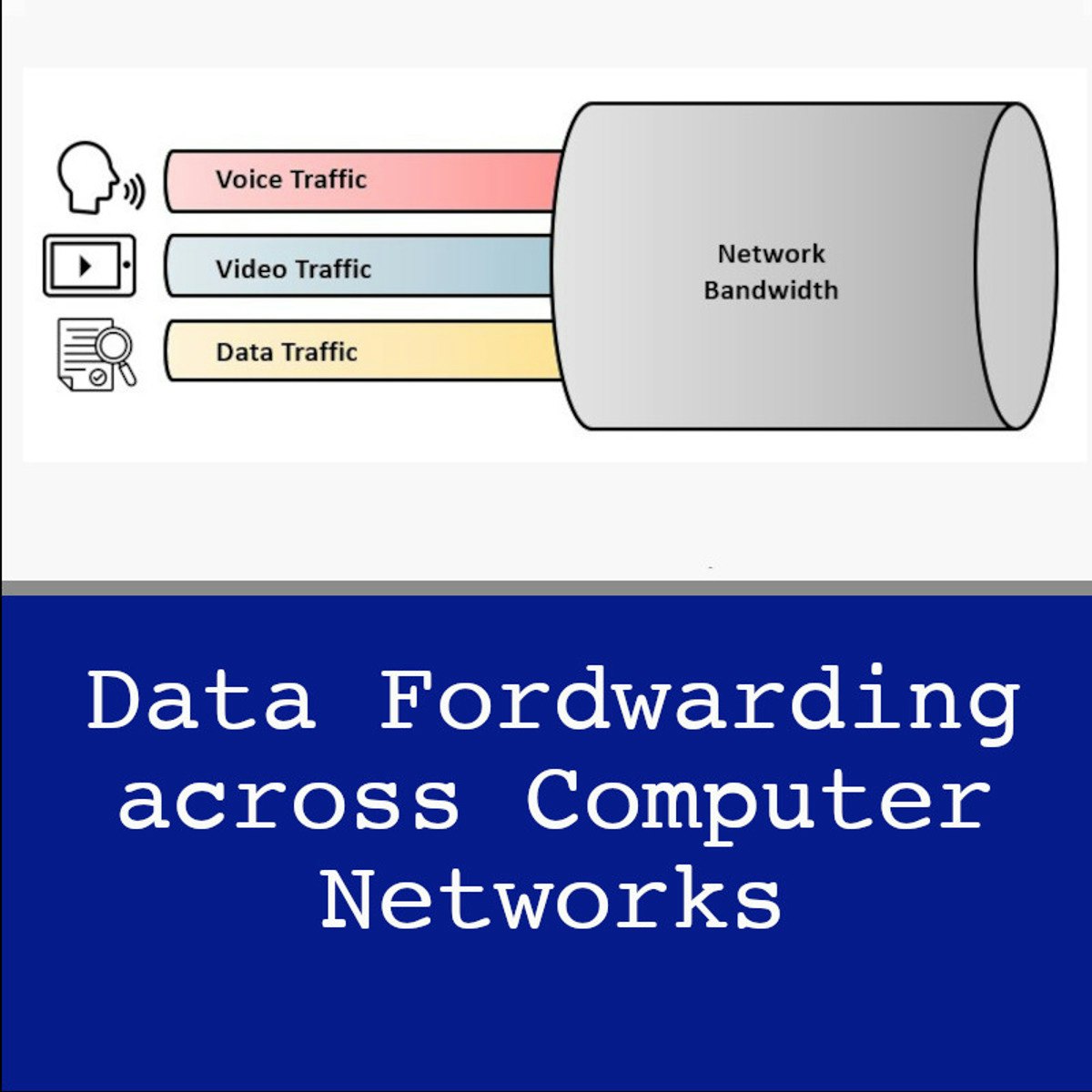
Data Forwarding Across Computer Networks
Welcome to the CCNA 1.3: Data Forwarding Across Computer Networks. This project is the third in the guided-projects series that is designed to help you acquire the hands-on skills required to pass the CCNA certification exam.
In this 2-hours guided project, you will understand how data is forwarded across computer networks, configure default and static routes on Cisco routers, set up dynamic routing using OSPF routing protocol, and verify and trace network routes.

Machine Learning for Telecom Customers Churn Prediction
In this hands-on project, we will train several classification algorithms such as Logistic Regression, Support Vector Machine, K-Nearest Neighbors, and Random Forest Classifier to predict the churn rate of Telecommunication Customers. Machine learning help companies analyze customer churn rate based on several factors such as services subscribed by customers, tenure rate, and payment method. Predicting churn rate is crucial for these companies because the cost of retaining an existing customer is far less than acquiring a new one.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.
Probabilistic Graphical Models 3: Learning
Probabilistic graphical models (PGMs) are a rich framework for encoding probability distributions over complex domains: joint (multivariate) distributions over large numbers of random variables that interact with each other. These representations sit at the intersection of statistics and computer science, relying on concepts from probability theory, graph algorithms, machine learning, and more. They are the basis for the state-of-the-art methods in a wide variety of applications, such as medical diagnosis, image understanding, speech recognition, natural language processing, and many, many more. They are also a foundational tool in formulating many machine learning problems.
This course is the third in a sequence of three. Following the first course, which focused on representation, and the second, which focused on inference, this course addresses the question of learning: how a PGM can be learned from a data set of examples. The course discusses the key problems of parameter estimation in both directed and undirected models, as well as the structure learning task for directed models. The (highly recommended) honors track contains two hands-on programming assignments, in which key routines of two commonly used learning algorithms are implemented and applied to a real-world problem.

Cyber Threats and Attack Vectors
Data breaches occur nearly every day. From very large retailers, down to your fantasy football website, and anywhere in between, they have been compromised in some way. How did the attackers get in? What did they do with the data they compromised? What should I be concerned with in my own business or my systems? This course is the second course in the Practical Computer Security. It will discuss types of threats and attack vectors commonly seen in today’s environment. I hate to be the bearer of bad news, but threats are all over the place! This course isn’t designed to insight fear that there is no hope for keeping systems and business secure, but rather educate you on how attacks are carried out so that you have a better sense of what to look out for in your business or with your systems.
Identifying, Monitoring, and Analyzing Risk and Incident Response and Recovery
Risk Identification, Monitoring, and Analysis: In the Risk Identification, Monitoring, and Analysis session, you will learn how to identify, measure, and control losses associated with adverse events. You will review, analyze, select, and evaluate safeguards for mitigating risk.You will learn processes for collecting information, providing methods of identifying security events, assigning priority levels, taking the appropriate actions, and reporting the findings to the correct individuals. After collection of the details from monitoring, we can analyze to determine if the system is being operated in accordance with accepted industry practices, and in compliance with organization policies and procedures.
Incident Response and Recovery: In the Incident Response and Recovery Session, you will gain an understanding of how to handle incidents using consistent, applied approaches in order to resolve. Once an incident is identified, action will be necessary in order to resolve. We will examine processes such as damage recovery, data integrity and preservation, and the collection, handling, reporting, and prevention. You will be introduced to the Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP) concepts and how they can be utilized in order to mitigate damages, recover business operations, and avoid critical business interruption. Through the use of the DRP, you will understand the procedures for emergency response and post-disaster recovery.
Course Objectives
1. Describe the risk management process
2. Perform security assessment activities
3. Describe processes for operating and maintaining monitoring systems
4. Identify events of interest
5. Describe the various source systems
6. Interpret reporting findings from monitoring results
7. Describe the incident handling process
8. Contribute to the incident handling process based upon role within the organization
9. Describe the supporting role in forensics investigation processes
10. Describe the supporting role in the business continuity planning process
11. Describe the supporting role in the disaster recovery planning process

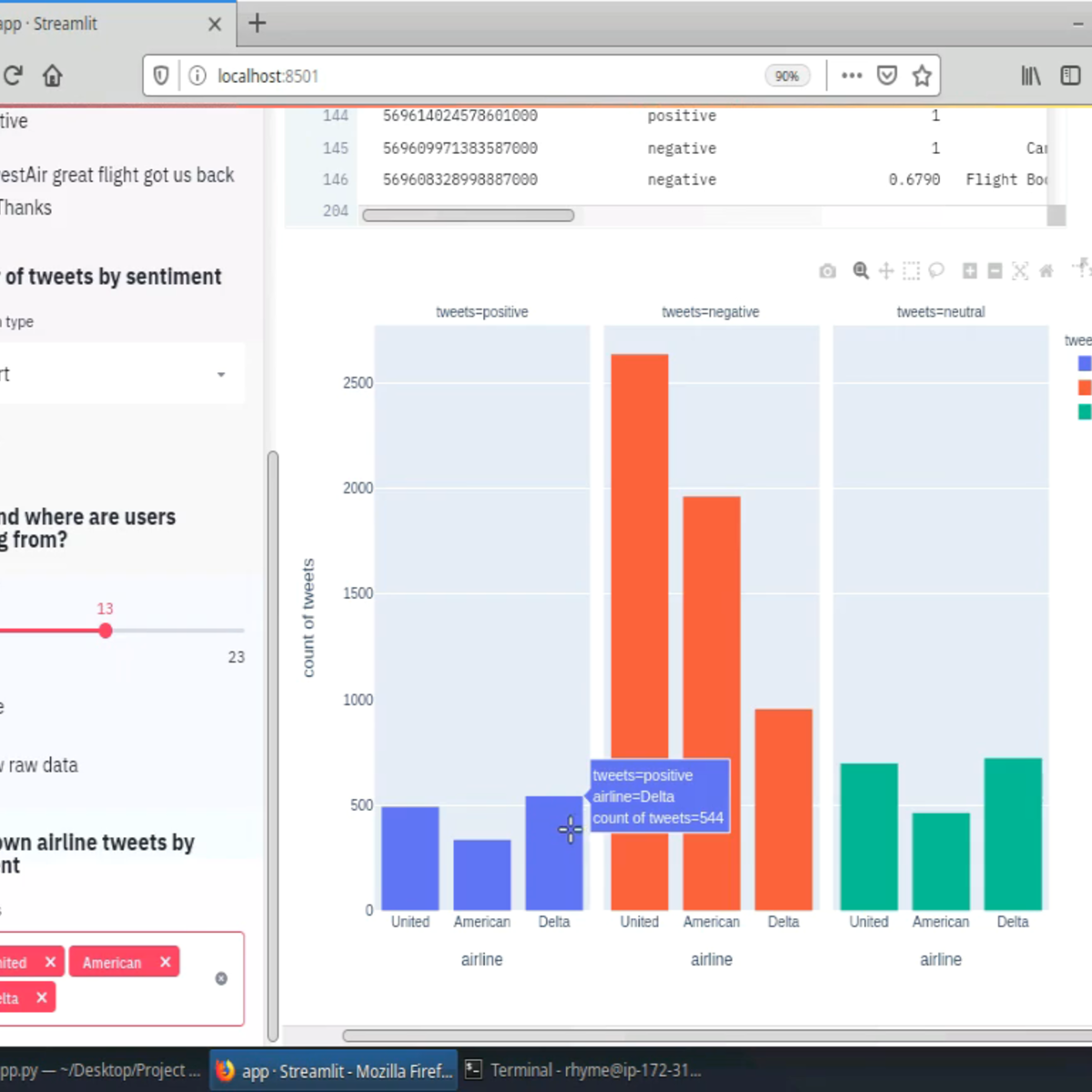
Create Interactive Dashboards with Streamlit and Python
Welcome to this hands-on project on building your first interactive, data dashboard with the Streamlit library in Python. By the end of this project, you are going to be comfortable with using Python and Streamlit to build beautiful and interactive dashboards and web apps, all with zero web development experience! We are going to load, explore, visualize and interact with data, and generate dashboards in less than 150 lines of Python code!
Prior experience with writing simple Python scripts and using pandas for data manipulation is recommended.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.
Popular Internships and Jobs by Categories
Browse
© 2024 BoostGrad | All rights reserved


