Back to Courses





Information Technology Courses - Page 96
Showing results 951-960 of 1471

Google Cloud Pub/Sub: Qwik Start - Python
This is a self-paced lab that takes place in the Google Cloud console.
In this lab, you learn about Pub/Sub and how to create a topic and subscriber with a Python script, and then publish and view messages. Watch the short video Simplify Event Driven Processing with Cloud Pub/Sub.

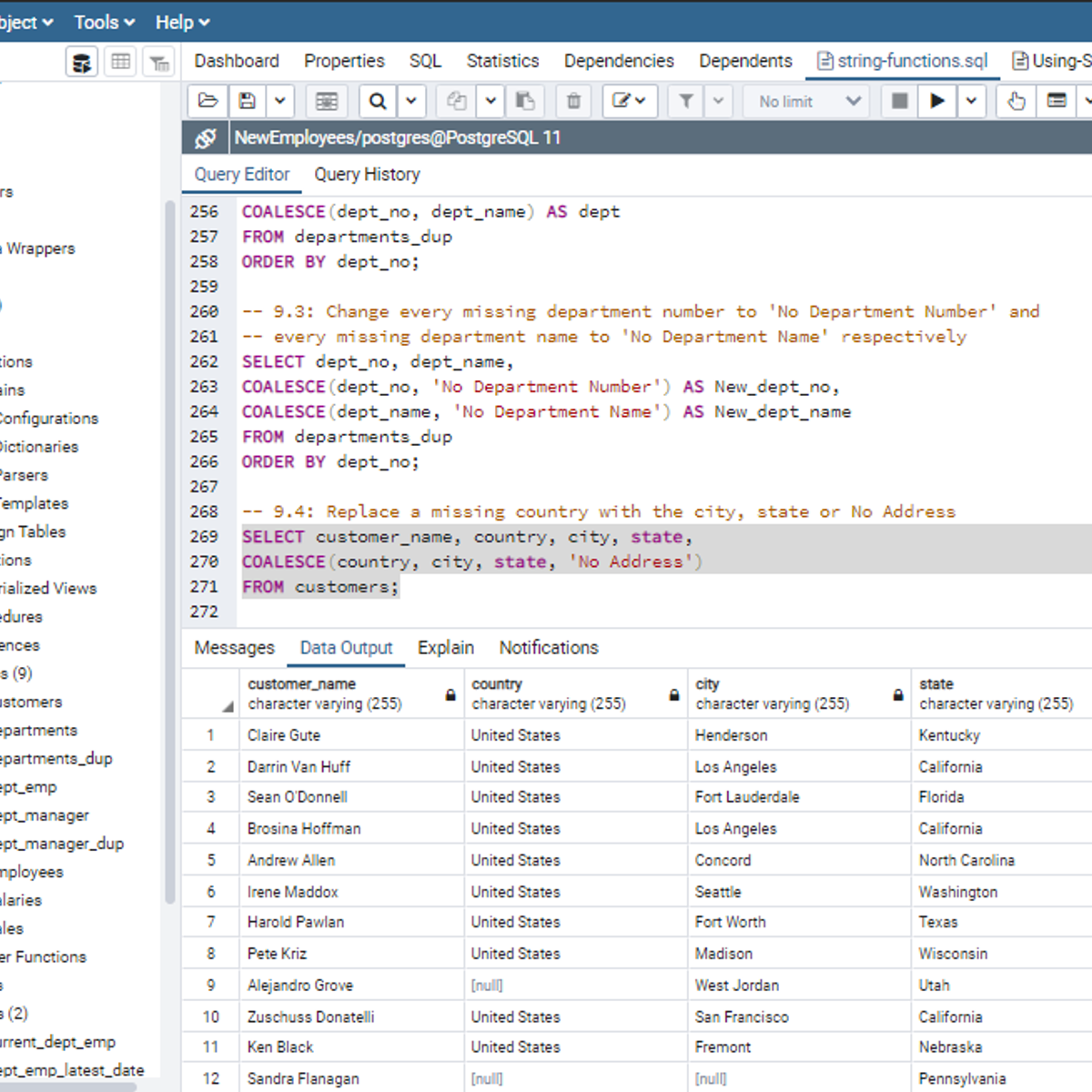
Using SQL String Functions to Clean Data
Welcome to this project-based course on Using SQL String Functions to Clean Data. In this project, you will learn how to perform data cleaning and manipulation using SQL string functions like LENGTH, UPPER & LOWER, REPLACE, TRIM, SUBSTRING, CONCAT, STRING_AGG, and COALESCE.
By the end of this 2-hour long project, you will understand why you need to learn about string functions and use them to get the desired result you want from tables in a database. Also, for this hands-on project, we will use PostgreSQL as our preferred database management system (DBMS). Therefore, to complete this project, it is required that you have prior experience with using PostgreSQL. Similarly, this project is an advanced SQL concept; so, a good foundation for writing SQL queries is vital to complete this project.
If you are not familiar with SQL and want to learn the basics, start with my previous guided projects titled “Performing Data definition and Manipulation in SQL" and “Querying Databases using SQL SELECT statement.” I taught these guided projects using PostgreSQL. Taking these projects will give the needed requisite to complete this project Using SQL String Functions to Clean Data. However, if you are comfortable writing queries in PostgreSQL, please join me on this wonderful ride! Let’s get our hands dirty!

Manage Your Versions with Git (Part II)
This 1.5-hour project-based course is the second part of "Manage Your Versions with Git". In this course, you will learn about branching, merging and remote repositories. At the end of this class, you will be able to collaborate with other developers all over the world using Git.
No specific coding experience is required but completion of Part I of this course is strongly recommended. Basic software development experience would be highly beneficial.

Cloud Network Security with Cloud IDS and VM-Series
This is a self-paced lab that takes place in the Google Cloud console. In this lab, you will learn about the Enhanced Layered Network Security Approach for Google Cloud with Cloud IDS and VM-Series.

Introduction to MongoDB
This course will get you up and running with MongoDB quickly, and teach you how to leverage its power for data analytics.
We'll start by mastering the fundamentals of MongoDB, including MongoDB’s Document data model, importing data into a cluster, working with our CRUD API and Aggregation Framework. These topics will be taught through a demo application which will give you a great first encounter of how simple and practical it can be to build applications with MongoDB.
In addition to these essential topics, you will also learn and work with useful MongoDB tools and services. You will work with Atlas, MongoDB's database as a service, MongoDB Compass, a schema visualization tool, as well as many other useful command-line utilities.

Enterprise System Management and Security
The world runs on computers. Your watch, your TV, your car. You might be familiar on how to operate each of these. Your home computer you are even more familiar with operating it. But what does it take to really take computer systems to the next level? - The enterprise level. In this course we discuss what makes home computing systems different from enterprise computing systems. This course will also help you prepare and design your own home lab to explore enterprise operating systems.
This course is for anyone who is exploring what it might take to have a job as a system administrator or for those who are already specialized in one area of system management and would like to move to another. This course may also be for those who are looking to understand how computer security plays an important role in system management.
At the end of the course, you will also be able to illustrate how different enterprise technologies play role in computing at an enterprise level. You will also be able to discuss the three pillars of the CIA triad and how they apply to enterprise systems.
While there is no technical and software component installs necessary for the completion of this course, supplemental how-to guides will be provided if you wish to follow along on the technical portion presented during the course.

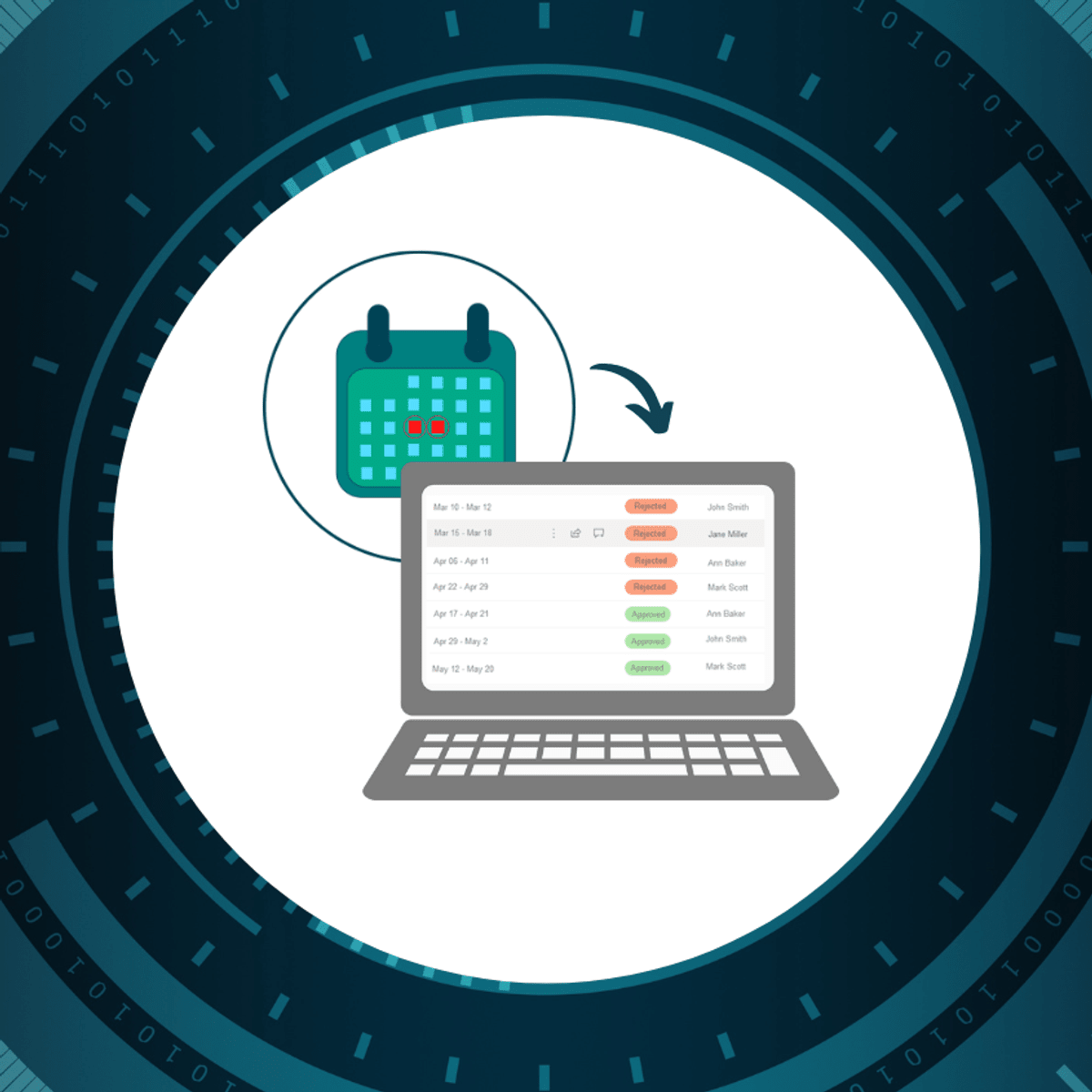
Book Vacation with Power Automate Multilevel Approval Flow
Whether you work in a small or large company, automation of booking vacation days by creating an approval process is a good idea to save time. This project can help you reduce correspondence by e-mail with your supervisors to just a few clicks. When employees want to book a vacation, they will create a request on SharePoint and their supervisors can approve it with one click.
In this beginner-level guided project "Book Vacation with Power Automate Multilevel Approval Flow", we will create a SharePoint site and a SharePoint list that will contain data about vacation requests, and we will create an automated flow using the approval actions. So, when an employee wants to book a vacation, they create a request on the SharePoint list and the flow that starts up the approval process gets triggered. When the supervisor approves or rejects the request, the employee receives an email with that information.
The requirement for this project is having a Microsoft developer program account, but don’t worry, you will be given instructions on how to get it right here.
If you are ready to make your and your colleagues’ lives easier by starting to automate manual, time-consuming processes, then this project is for you! Let's get started!

Deploy a Website Container Image in AWS ECS and AWS Fargate
In this one hour project, you will learn how to build a docker image containing a website, push in AWS Elastic Container Registry repository and deploy and run in AWS Elastic Container Service and AWS Fargate.
Containerization is an approach to software development in which an application or service, its dependencies, and its configuration are packaged together as a container image. The containerized application can be tested as a unit and deployed as a container image instance to the host operating system (OS).
Containers also isolate applications from each other on a shared OS. Containerized applications run on top of a container host that in turn runs on the OS (Linux or Windows). Containers, therefore, have a significantly smaller footprint than virtual machine images.
In this scenario, AWS offers some services that allow us to deploy and use containerized applications in the Cloud.
Once you're done with this project, you will be able to deploy a single container in AWS as well as a group of containers managed by a Load Balancer in just a few steps.

SQL for Data Science with R
Much of the world's data resides in databases. SQL (or Structured Query Language) is a powerful language which is used for communicating with and extracting data from databases. A working knowledge of databases and SQL is a must if you want to become a data scientist.
The purpose of this course is to introduce relational database concepts and help you learn and apply foundational knowledge of the SQL and R languages. It is also intended to get you started with performing SQL access in a data science environment.
The emphasis in this course is on hands-on and practical learning. As such, you will work with real databases, real data science tools, and real-world datasets. You will create a database instance in the cloud. Through a series of hands-on labs, you will practice building and running SQL queries. You will also learn how to access databases from Jupyter notebooks using SQL and R.
No prior knowledge of databases, SQL, R, or programming is required.
Anyone can audit this course at no charge. If you choose to take this course and earn the Coursera course certificate, you can also earn an IBM digital badge upon successful completion of the course.

In the Trenches: Security Operations Center
Cyber-attacks, breaches, and incidents continue to grow. The sophistication and complexity of these attacks continue to evolve. More than ever organizations need to plan, prepare, and defend against a potential cyber incident. Security Operation Centers (SOCs) act as an organization's front-line defense against cyber incidents. SOC analyst accomplishes this by monitoring and responding to network and host anomalies, performing an in-depth analysis of suspicious events, and when necessary, aiding in forensic investigations.
This course is designed to be a primer for anyone planning on taking the EC-Council CSA course. We will discuss the structure, organization, and general daily activities of SOC analysts. We will also look at several defensive tools including SEIMs, IDS, and IPS. We will talk about event monitoring and vulnerability management. Finally, we will talk about what to expect when an incident happens.
Popular Internships and Jobs by Categories
Browse
© 2024 BoostGrad | All rights reserved


