Back to Courses







Computer Science Courses - Page 97
Showing results 961-970 of 2309

C Programming: Advanced Data Types - 5
In this course you will define your own data types in C, and use the newly created types to more efficiently store and process your data.
Many programming languages provide a number of built-in data types to store things such as integers, decimals, and characters in variables, but what if you wanted to store more complex data?
Defining your own data types in C allows you to more efficiently store and process data such as a customer's name, age and other relevant data, all in one single variable! You will also gain experience with programming concepts that are foundational to any programming language.
Why learn C and not another programming language? Did you know that smartphones, your car’s navigation system, robots, drones, trains, and almost all electronic devices have some C-code running under the hood? C is used in any circumstance where speed and flexibility are important, such as in embedded systems or high-performance computing.
At the end of this short course, you will reach the fifth milestone of the C Programming with Linux Specialization, unlocking the door to a career in computer engineering.
Your job Outlook:
- Programmers, developers, engineers, managers, and related industries within scientific computing and data science;
- Embedded systems such as transportation, utility networks, and aerospace;
- Robotics industry and manufacturing;
- IoT (Internet of Things) used in smart homes, automation, and wearables.
- IEEE, the world’s largest technical professional organization for the advancement of technology, ranks C as third of the top programming languages of 2021 in demand by employers. (Source: IEEE Spectrum)
This course has received financial support from the Patrick & Lina Drahi Foundation.

Classical Cryptosystems and Core Concepts
Welcome to Introduction to Applied Cryptography. Cryptography is an essential component of cybersecurity. The need to protect sensitive information and ensure the integrity of industrial control processes has placed a premium on cybersecurity skills in today’s information technology market. Demand for cybersecurity jobs is expected to rise 6 million globally by 2019, with a projected shortfall of 1.5 million, according to Symantec, the world’s largest security software vendor. According to Forbes, the cybersecurity market is expected to grow from $75 billion in 2015 to $170 billion by 2020. In this specialization, you will learn basic security issues in computer communications, classical cryptographic algorithms, symmetric-key cryptography, public-key cryptography, authentication, and digital signatures. These topics should prove especially useful to you if you are new to cybersecurity Course 1, Classical Cryptosystems, introduces you to basic concepts and terminology related to cryptography and cryptanalysis. It is recommended that you have a basic knowledge of computer science and basic math skills such as algebra and probability.

How to integrate apps into Hootsuite dashboard
At the end of this project, you will have all the basic skills to integrate apps into your Hootsuite Dashboard. You will be able to discover the different types of apps that you can install and you will be able to easily and quickly integrate them into your dashboard on Hootsuite.

Cybersecurity for Everyone
Cybersecurity affects everyone, including in the delivery of basic products and services. If you or your organization want to better understand how to address your cybersecurity, this is the course for you and your colleagues to take -- from seasoned professionals to your non-technical colleagues.
Your instructor, Dr. Charles Harry, has served on the front lines with the NSA (National Security Agency) and as an expert advising corporate and institutional leaders on managing cybersecurity risk. And he brings a rare and engaging perspective to help you learn cybersecurity from the ground up.
Cybersecurity for Everyone lays the groundwork to understand and explore the key issues facing policy makers attempting to manage the problem of cybersecurity, from its technical foundations to the domestic and international policy considerations surrounding governance, privacy, and risk management, to applications for achieving the goals of an enterprise, an institution, or a nation. This course is designed for students with some or no background in information technology, whether a novice or active in the cybersecurity field (engineers and computer scientists will learn the broader context and business aspects of cybersecurity), and will provide the principles to understand the current debates shaping a rapidly evolving security landscape.

Python Scripting for DevOps
In this course, we are going to focus on the following learning objectives:
1. Work with core Python programming tools
2. Become comfortable reading and writing Python scripts
By the end of this course, you will have a solid grasp of scripting in Python. You will learn the Pythonic way of many of the core programming concepts. You will be able to read and understand Python scripts in your daily line of work

The Business of Cybersecurity Capstone
This course intends to make the student familiar with information security management. When you have finished with this course you will know more about:
• Governance: including the mission, roles and responsibilities of the InfoSec governance function, and the strategic planning process and InfoSec’s role in the organization’s strategic planning effort.
• You will understand the various types of InfoSec policies and how effective information security policy is created and used.
• Risk management and the risk management process
• Certain laws and ethical issues impacting information security in the organization. And some common information security management practices such as benchmarking and performance measures.

Java Programming: Build a Recommendation System
Ever wonder how Netflix decides what movies to recommend for you? Or how Amazon recommends books? We can get a feel for how it works by building a simplified recommender of our own!
In this capstone, you will show off your problem solving and Java programming skills by creating recommender systems. You will work with data for movies, including ratings, but the principles involved can easily be adapted to books, restaurants, and more. You will write a program to answer questions about the data, including which items should be recommended to a user based on their ratings of several movies. Given input files on users ratings and movie titles, you will be able to:
1. Read in and parse data into lists and maps;
2. Calculate average ratings;
3. Calculate how similar a given rater is to another user based on ratings; and
4. Recommend movies to a given user based on ratings.
5. Display recommended movies for a given user on a webpage.

Create a C# Class Definition to Track Employee Data
By the end of this project, you will create an application that defines an Employee class and create one to many Employee object instances.
Object Oriented programming in languages such as C# is advantageous because it allows the programmer to think in terms of the way people think of the real world, in terms of Objects like employees, airplanes, and homes for example.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

System Validation (2): Model process behaviour
System Validation is the field that studies the fundamentals of system communication and information processing. It is the next logical step in computer science and improving software development in general. It allows automated analysis based on behavioural models of a system to see if a system works correctly. We want to guarantee that the systems does exactly what it is supposed to do. The techniques put forward in system validation allow to prove the absence of errors. It allows to design embedded system behaviour that is structurally sound and as a side effect enforces you to make the behaviour simple and insightful. This means that the systems are not only behaving correctly, but are also much easier to maintain and adapt. ’Model process behaviour' is the follow up MOOC to 'Automata and behavioural equivalences'. This MOOC shows you how to model process behaviour, in particular protocols and distributed algorithms, dive deeper in the properties of system behaviour, and keep things simple to avoid a state space explosion. Reading material. J.F. Groote and M.R. Mousavi. Modeling and analysis of communicating systems. The MIT Press, 2014.
This course is part 2 of the set of courses for System Validation. System Validation, as a set of courses, is part of a larger EIT Digital online programme called 'Internet of Things through Embedded Systems'.

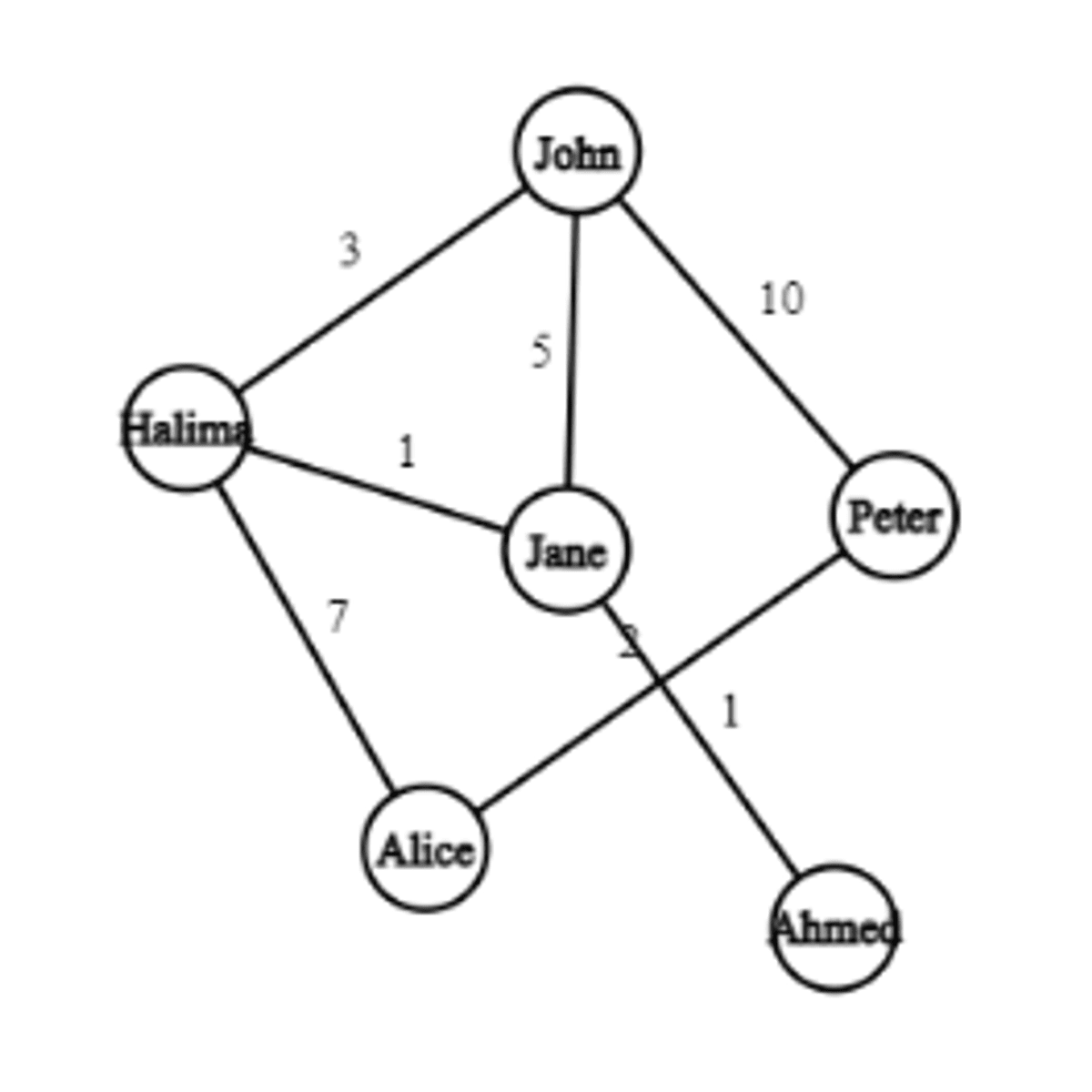
Create a Network of Friends using a Weighted Graph in Java
The learner will create user-defined methods to create a network of friends using a weighted undirected graph. The learner will implement a graph using a Hashmap of nodes and Linked Lists, add nodes to the graph, add edges between nodes, print the contents of the graph, and traverse the graph using depth-first search.
