Back to Courses






Computer Science Courses - Page 152
Showing results 1511-1520 of 2309

Enterprise System Management and Security
The world runs on computers. Your watch, your TV, your car. You might be familiar on how to operate each of these. Your home computer you are even more familiar with operating it. But what does it take to really take computer systems to the next level? - The enterprise level. In this course we discuss what makes home computing systems different from enterprise computing systems. This course will also help you prepare and design your own home lab to explore enterprise operating systems.
This course is for anyone who is exploring what it might take to have a job as a system administrator or for those who are already specialized in one area of system management and would like to move to another. This course may also be for those who are looking to understand how computer security plays an important role in system management.
At the end of the course, you will also be able to illustrate how different enterprise technologies play role in computing at an enterprise level. You will also be able to discuss the three pillars of the CIA triad and how they apply to enterprise systems.
While there is no technical and software component installs necessary for the completion of this course, supplemental how-to guides will be provided if you wish to follow along on the technical portion presented during the course.

Facial Expression Classification Using Residual Neural Nets
In this hands-on project, we will train a deep learning model based on Convolutional Neural Networks (CNNs) and Residual Blocks to detect facial expressions. This project could be practically used for detecting customer emotions and facial expressions.
By the end of this project, you will be able to:
- Understand the theory and intuition behind Deep Learning, Convolutional Neural Networks (CNNs) and Residual Neural Networks.
- Import Key libraries, dataset and visualize images.
- Perform data augmentation to increase the size of the dataset and improve model generalization capability.
- Build a deep learning model based on Convolutional Neural Network and Residual blocks using Keras with Tensorflow 2.0 as a backend.
- Compile and fit Deep Learning model to training data.
- Assess the performance of trained CNN and ensure its generalization using various KPIs.
- Improve network performance using regularization techniques such as dropout.

Deploy a Website Container Image in AWS ECS and AWS Fargate
In this one hour project, you will learn how to build a docker image containing a website, push in AWS Elastic Container Registry repository and deploy and run in AWS Elastic Container Service and AWS Fargate.
Containerization is an approach to software development in which an application or service, its dependencies, and its configuration are packaged together as a container image. The containerized application can be tested as a unit and deployed as a container image instance to the host operating system (OS).
Containers also isolate applications from each other on a shared OS. Containerized applications run on top of a container host that in turn runs on the OS (Linux or Windows). Containers, therefore, have a significantly smaller footprint than virtual machine images.
In this scenario, AWS offers some services that allow us to deploy and use containerized applications in the Cloud.
Once you're done with this project, you will be able to deploy a single container in AWS as well as a group of containers managed by a Load Balancer in just a few steps.

FPGA computing systems: Partial Dynamic Reconfiguration
New application domains demand ever increasing adaptability and performance. In order to cope with changing user requirements, improvements in system features, changing protocol and data-coding standards, and demands for support of a variety of different user applications, many emerging applications in communication, computing and consumer electronics demand that their functionality stays flexible after the system has been manufactured. Reconfigurable Systems-on-a-Chips (SoCs) employing different microprocessor cores and different types of reconfigurable fabrics are one attractive solution for these domains. The increasing prominence of reconfigurable devices within such systems requires HW/SW co-design for SoCs to address the trade-off between software execution and reconfigurable hardware acceleration. Dynamic reconfiguration capabilities of current reconfigurable devices create an additional dimension in the temporal domain. During the design space exploration phase, overheads associated with reconfiguration and hardware/software interfacing need to be evaluated carefully in order to harvest the full potential of dynamic reconfiguration.
The course will introduce the student with the concept of reconfigurability in FPGAs, presenting the available mechanisms and technologies at the device level and the tools and design methodologies required to design reconfigurable FPGA-based systems. The course will present the different aspects of the design of FPGA-based reconfigurable systems, focusing in particular on dynamically self-reconfigurable systems. The design methodologies and tools required to design a dynamically-reconfigurable system will be introduced and described, together with the problems that need to be considered.

University Admission Prediction Using Multiple Linear Regression
In this hands-on guided project, we will train regression models to find the probability of a student getting accepted into a particular university based on their profile. This project could be practically used to get the university acceptance rate for individual students using web application.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Terraform Basics - Create a virtual machine on MS Azure
Terraform allows you to define and create complete infrastructure deployments in MS Azure. You build Terraform templates in a human-readable format that creates and configure Azure resources in a consistent, reproducible manner.

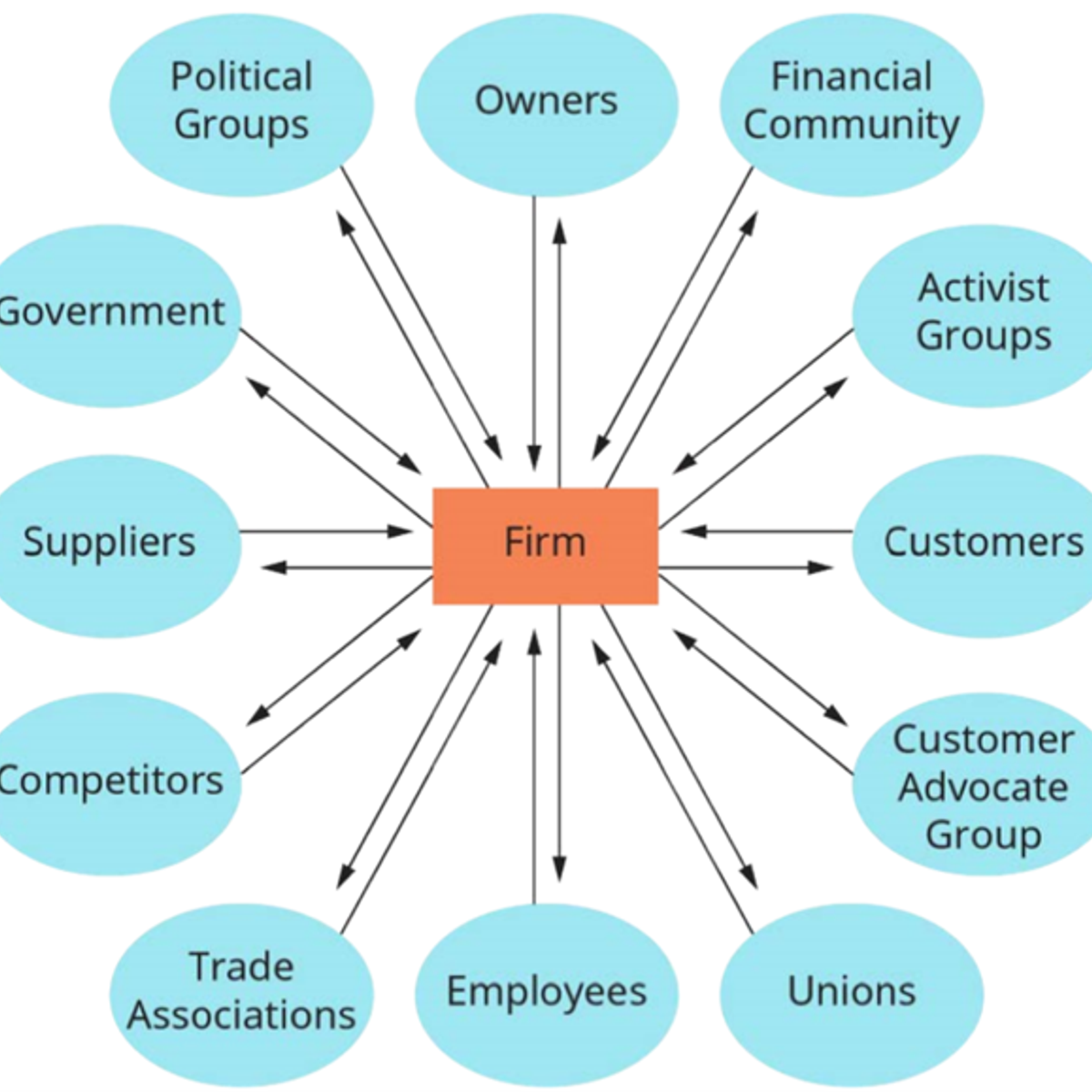
Involve Critical Players with Stakeholder Maps in Miro
By the end of this project, you will be able to identify critical players within a stakeholder map.
To do this, you will gain hands-on experience applying design thinking and user experience research to align the right stakeholders with their influence upon project success in the Miro online visual collaboration platform for teamwork.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Prototyping and Design
In this course you will learn how to design and prototype user interfaces to address the users and tasks identified in user research. Through a series of lectures and exercises, you will learn and practice paper- and other low-fidelity prototyping techniques; you will learn and apply principles from graphic design, including design patterns; you will learn to write a design rationale; and you will learn how to design for specific populations and situations, including principles and practices of accessible design.

Learn Fundamentals Of Computer Programming With C Language
In this 1.5-hour long project-based course, you will get introduced to C programming language and you will learn basics of C language.
By the end of this project you will be able to build a basic console C application.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Technical Deep Dive with Incident Response Tools
The Cyber Incident Response course will give students an understanding of how incidents are responded to at a high level, as well as allow them to build important technical skills through the hands-on labs and projects.
This course starts with a high-level discussion of what happens at each phase of responding to an incident, followed by a technical deep dive into some of the more exciting parts of memory, network, and host analysis and forensics. This course is for anyone wishing to apply learned forensics and offensive knowledge such as ethical hacking to the incident response process.
