Back to Courses







Computer Science Courses - Page 148
Showing results 1471-1480 of 2309

Manage Docker Networking
If you use Docker to develop and deploy apps, then learning about Docker's built-in networking capabilities could be valuable to you. It is possible to simulate a networked environment using Docker. You would not have to purchase and set up expensive hardware, and that would save you time and money.
In this project, you will pretend to be the employee of a fictional company named Acme. You will learn about creating a Docker network, running containers so that they join a particular network, inspecting network objects, testing connectivity, and managing networked containers. There are also two optional hands-on practice activities to help you learn these new skills with confidence.
Machine Learning for All
Machine Learning, often called Artificial Intelligence or AI, is one of the most exciting areas of technology at the moment. We see daily news stories that herald new breakthroughs in facial recognition technology, self driving cars or computers that can have a conversation just like a real person. Machine Learning technology is set to revolutionise almost any area of human life and work, and so will affect all our lives, and so you are likely to want to find out more about it. Machine Learning has a reputation for being one of the most complex areas of computer science, requiring advanced mathematics and engineering skills to understand it. While it is true that working as a Machine Learning engineer does involve a lot of mathematics and programming, we believe that anyone can understand the basic concepts of Machine Learning, and given the importance of this technology, everyone should. The big AI breakthroughs sound like science fiction, but they come down to a simple idea: the use of data to train statistical algorithms. In this course you will learn to understand the basic idea of machine learning, even if you don't have any background in math or programming. Not only that, you will get hands on and use user friendly tools developed at Goldsmiths, University of London to actually do a machine learning project: training a computer to recognise images. This course is for a lot of different people. It could be a good first step into a technical career in Machine Learning, after all it is always better to start with the high level concepts before the technical details, but it is also great if your role is non-technical. You might be a manager or other non-technical role in a company that is considering using Machine Learning. You really need to understand this technology, and this course is a great place to get that understanding. Or you might just be following the news reports about AI and interested in finding out more about the hottest new technology of the moment. Whoever you are, we are looking forward to guiding you through you first machine learning project.
NB this course is designed to introduce you to Machine Learning without needing any programming. That means that we don't cover the programming based machine learning tools like python and TensorFlow.

Access Control Concepts
Welcome to course 3 of 5 of this Specialization, Access Control Concepts.
In Course 1, we introduced access control concepts. Now, we will take a more detailed look at the types of access control that every information security professional should be familiar with. We will discuss both physical and logical controls and how they are combined to strengthen the overall security of an organization. This is where we describe who gets access to what, why access is necessary, and how that access is managed.
After completing this course, the participant will be able to:
Select access controls that are appropriate in a given scenario.
- Relate access control concepts and processes to given scenarios.
- Compare various physical access controls.
- Describe logical access controls.
- Practice the terminology of access controls and review concepts of access controls.
Agenda
Course Introduction
Module 1: Key Concepts
Module 2: Administrative Controls
Module 3: Physical Controls
Module 4:Logical Controls
Module 5: Controls Review
This training is for IT professionals, career changers, college students, recent college graduates, advanced high school students and recent high school graduates looking to start their path toward cybersecurity leadership by taking the Certified in Cybersecurity entry-level exam.
There are no prerequisites to take the training or the exam. It is recommended that candidates have basic Information Technology (IT) knowledge. No work experience in cybersecurity or formal education diploma/degree is required.

Embedded Software and Hardware Architecture
Embedded Software and Hardware Architecture is a first dive into understanding embedded architectures and writing software to manipulate this hardware. You will gain experience writing low-level firmware to directly interface hardware with highly efficient, readable and portable design practices. We will now transition from the Host Linux Machine where we built and ran code in a simulated environment to an Integrated Development Environment where you will build and install code directly on your ARM Cortex-M4 Microcontroller. Course assignments include writing firmware to interact and configure both the underlying ARM architecture and the MSP432 microcontroller platform. The course concludes with a project where you will develop a circular buffer data structure.
In this course you will need the Texas Instruments LaunchPad with the MSP432 microcontroller in order to complete the assignments. Later courses of the Specialization will continue to use this hardware tool to develop even more exciting firmware.

Benefits of Bootstrap
In this 1-hour long project-based course, you will learn what bootstrap is, the benefits of using bootstrap as a web developer, and the different features bootstrap has to offer.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Create Docker Container with Flask Seaborn Regression Plot App
Often a software application developed on one platform will not run on another because of software environment differences. Sometimes it can happen when an operating system is updated, for example. Suddenly an application starts to fail. Containers solve that problem by creating a controlled environment in which to run the application, separate from the host machine’s environment. The container contains a specific version of each software package that is known to work with an application at a given point in time. Docker is an application that allows the developer to generate containers to easily build and share applications.
In this course, you will create a Docker container in which you will implement a web application using flask in a Linux environment. The application will return a regression plot of data housed in a CSV file on the server.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.
Learn to Program: Crafting Quality Code
Not all programs are created equal. In this course, we'll focus on writing quality code that runs correctly and efficiently. We'll design, code and validate our programs and learn how to compare programs that are addressing the same task.

iOS App Capstone
In this capstone course, you’ll demonstrate your proficiency in your new skill set by creating a native iOS app.
By the end of this course, you’ll be able to:
-Build a native iOS mobile app
-Publish and sell it on the Apple Store
You’ll gain experience with the following tools and software:
-SwiftUI and MVC architecture
-APIs
-Core Data
-iOS development tools and environments
-Geolocation software
-Application design and development libraries

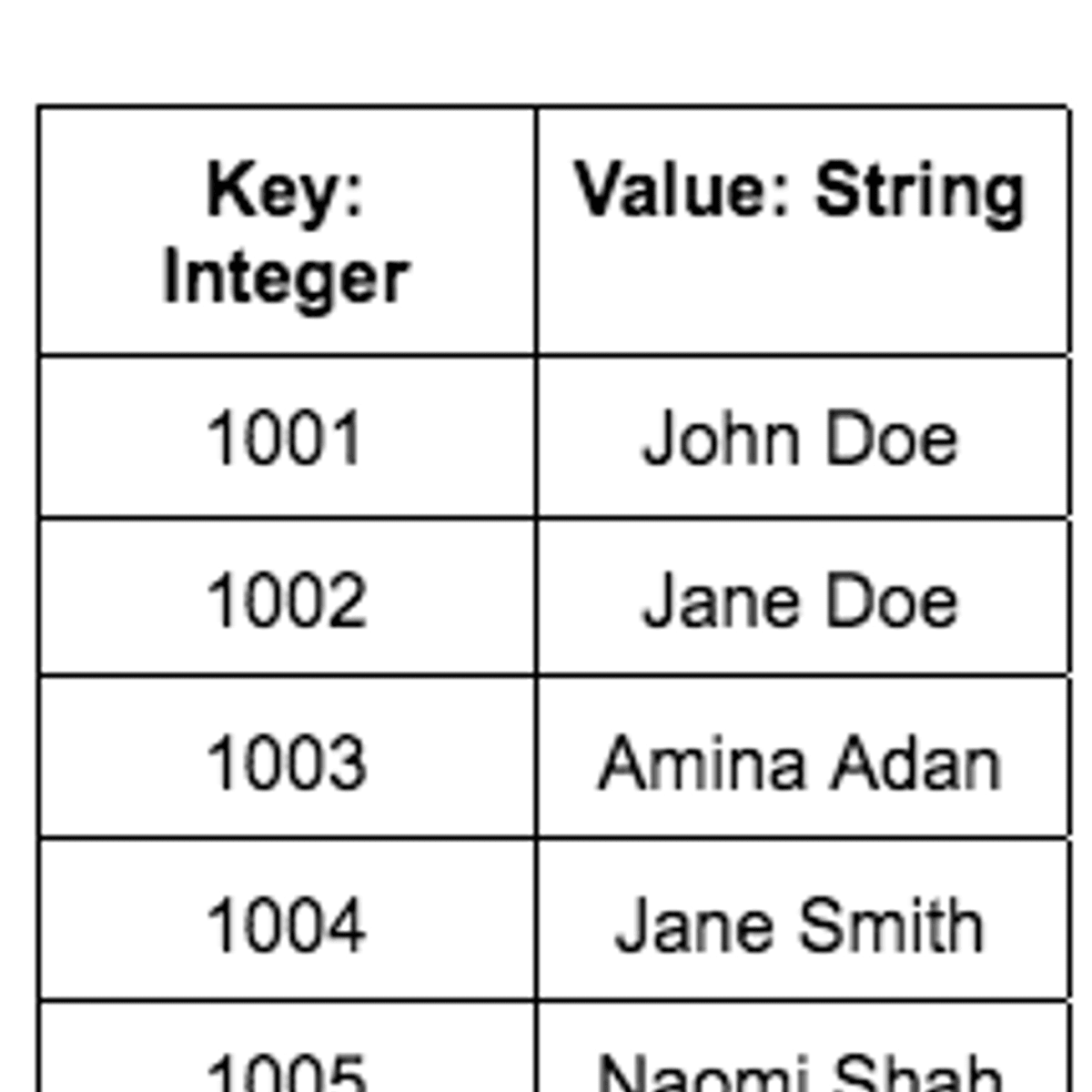
Create a simple record of student marks using Java HashMap
Create a simple record of student marks using Java HashMap

Working with Amazon DynamoDB using Python & Boto3
In this 2-hours long project, we will look at how to work with DynamoDB, a fully managed NoSQL Database provided by Amazon Web Services (AWS) using Python & Boto3. We will look at how to generate credentials to programmatically access AWS resources. We will then look at how to create a DynamoDB Table and load data in it. We will then move on to how to perform CRUD operations in DynamoDB which include Create new records, Reading, updating and deleting existing records.
We will then look at how to perform Queries to retrieve data from a table using the primary key. We will then look at Scan operation which reads every item in the entire table and look at how to apply filters on the retrieved data to retrieve data without using a primary key. Finally we will see how to create an Index, specifically Global Secondary Index (GSI), to perform queries (an efficient alternative to Scan) on the database using fields which are non-primary key.
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.
