Back to Courses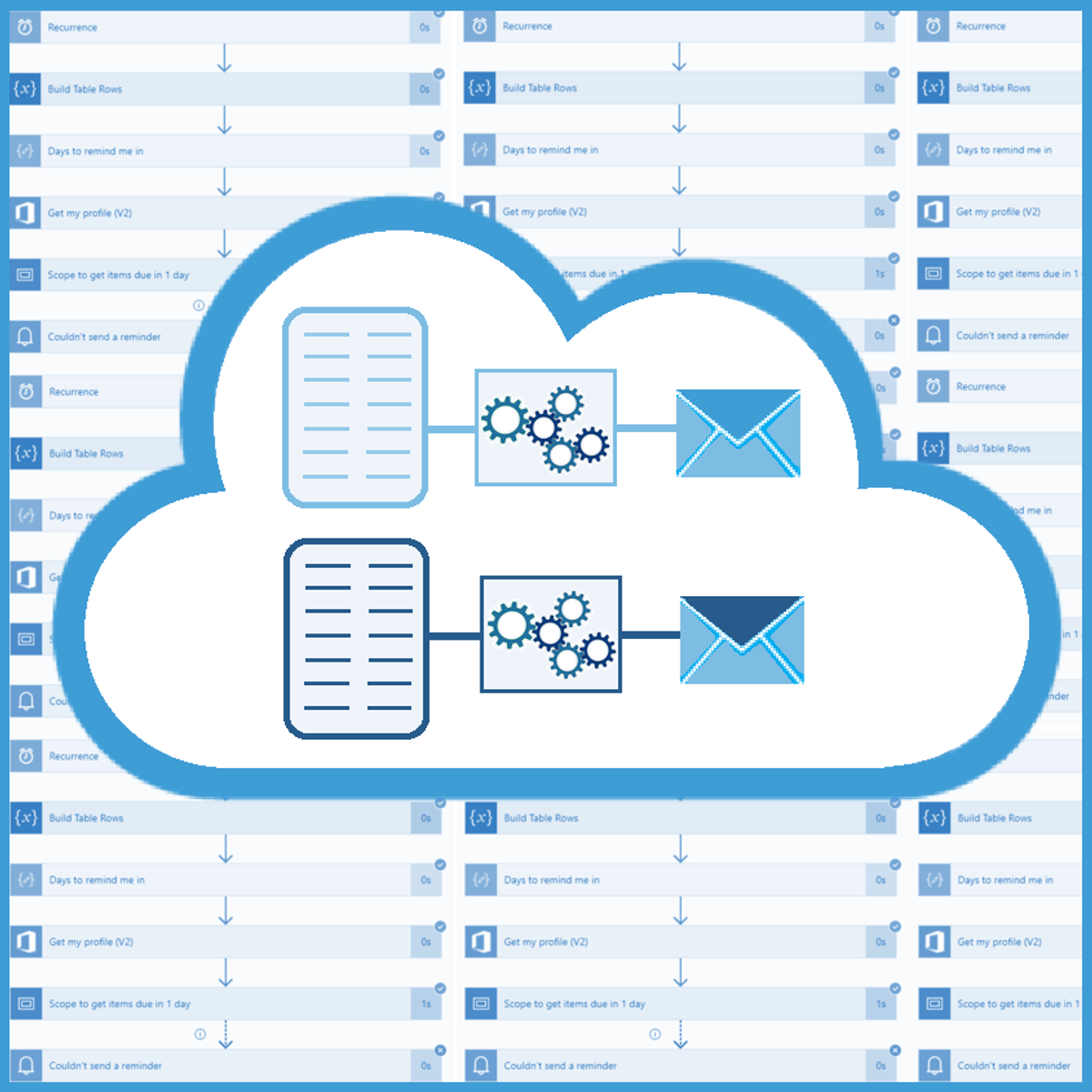







Information Technology Courses - Page 84
Showing results 831-840 of 1471

Use Power Automate & SharePoint to Automate Invoice Sending
Each company must produce invoices for their services and each invoice must be delivered to the client. Most companies have employees who are doing both tasks manually, first they create an invoice and then they send it by email to the customer. As with most other repetitive tasks, we can use Power Automate and SharePoint to automate one of those 2 tasks and that is, sending invoices by email. We just need to set up some rules, set up a SharePoint site as our data source and implement a Power Automate flow which will handle the process.
In this 40-minutes long guided project, “Use Power Automate & SharePoint to Automate Invoice Sending”, you will create a SharePoint site and list, set up a document library and create a Power Automate flow which will automate the sending of invoices to the customers. Of course, you can allow other colleagues to access and use this SharePoint site so they will be able to use your implementation as well. In the end, you won’t need to send emails to the customers manually, all you will have to do is create an invoice, name it correctly and upload it to the SharePoint document library and the Power Automate flow will do the rest.
Since this project uses Office 365 services like SharePoint and Power Apps (part of the Microsoft Power Platform), you will need access to a Microsoft account and a Microsoft 365 Developer Program subscription account. In the video at the beginning of the project you will be given instructions on how to sign up for both.
Intro to Operating Systems 2: Memory Management
Learn the inner workings of operating systems without installing anything!
This course is designed for learners who are looking to maximize performance by understanding how operating systems work at a fundamental level. The modules in this course cover segmentation, paging, swapping, and virtual memory.
To allow for a truly hands-on, self-paced learning experience, this course is video-free. Assignments contain short explanations with images and runnable code examples with suggested edits to explore code examples further, building a deeper understanding by doing. You’ll benefit from instant feedback from a variety of assessment items along the way, gently progressing from quick understanding checks (multiple choice, fill in the blank, and un-scrambling code blocks) to slowly building features, resulting in large coding projects at the end of the course.

Cloud and Wireless Security
Course 6: Cloud and Wireless Security
Welcome to course six. This course applies to security concepts, ideas, and considerations to two major changes that we have experienced in recent years. It's regarding the way we use the data. First, we use our data on the go. In other words, data services are provided to our mobile phones, Wi-Fi, and other devices. Second, many enhanced functions are implemented through services hosted in the cloud platform, where our data is stored or processed. Both transformations are complex topics. However, as a security practitioner, we can narrow these two topics by applying the security fundamentals to secure the data. This boils down to the three basics of protecting data at rest, in motion, and in use. The data is either on the endpoint devices, servers, or other endpoints, making these services a reality.
Course 6 Learning Objectives
After completing this course, the participant will be able to:
L6.1 - Recall cloud security concepts and configurations.
L6.2 - Recognize types of virtualization and cloud security considerations.
L6.3 - Summarize the types of telecommunications and network access controls.
Course Agenda
Module 1: Operate and Configure Cloud Security (Domain 7 - Systems and Application Security)
Module 2: Cloud Security Considerations (Domain 6 - Network and Communications Security)
Module 3: Secure Wireless Configurations (Domain 6 - Network and Communications Security)
Who Should Take This Course: Beginners
Experience Required: No prior experience required

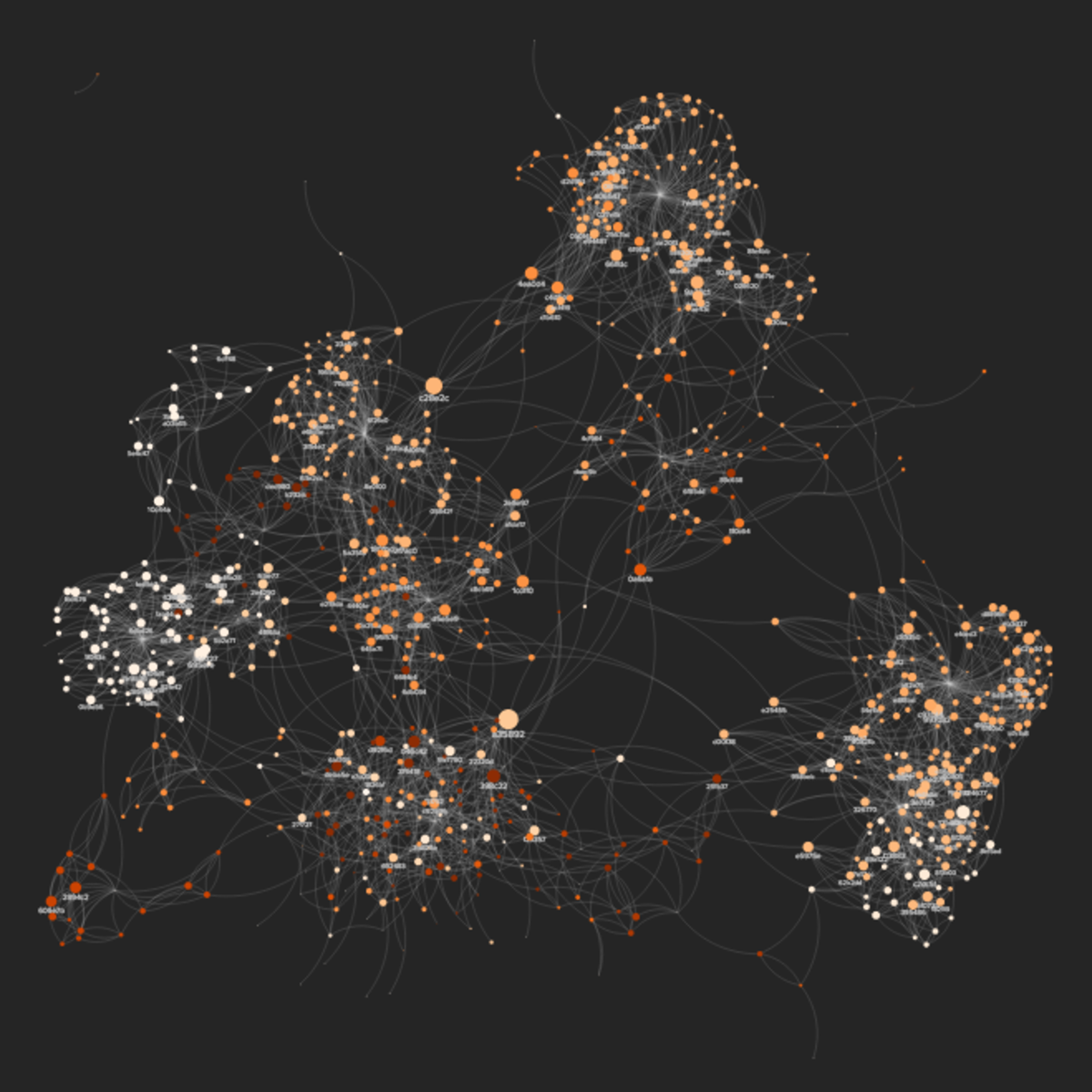
Introduction to Systems and Network Mapping with Kumu
In this 1-hour long project-based course, you will create an interactive multi-elements relationship map, as well as design visualizations for a real-world social network, based on metrics analyses.
Besides helping you to make sense of complex data, relationship maps like the ones we will build here are a great medium to visually present Causal Loop and Stock and Flow diagrams, as well as non-linear dynamics within an ecosystem.
This project will also introduce you to some of the basic concepts behind network theory, which will inform the analyses and interpretations of the maps you will create.
The art and craft of creating and communicating relationship maps is applicable to a wide range of areas, from design and software engineering, to organization consultancy and community building. And this project is an accessible opportunity for anyone to get some hands-on practice and knowledge on this subject. So let's map!
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

Penetration Testing, Incident Response and Forensics
This course gives you the background needed to gain Cybersecurity skills as part of the Cybersecurity Security Analyst Professional Certificate program.
You will learn about the different phases of penetration testing, how to gather data for your penetration test and popular penetration testing tools. Furthermore, you will learn the phases of an incident response, important documentation to collect, and the components of an incident response policy and team. Finally, you will learn key steps in the forensic process and important data to collect.
This course also gives you a first look at scripting and the importance to a system analyst.
This course is intended for anyone who wants to gain a basic understanding of Cybersecurity or as the fifth course in a series of courses to acquire the skills to work in the Cybersecurity field as a Cybersecurity Analyst.
The completion of this course also makes you eligible to earn the Penetration Testing, Incident Response and Forensics IBM digital badge. More information about the badge can be found https://www.youracclaim.com/org/ibm/badge/penetration-testing-incident-response-and-forensics.
In this course you will learn to:
• Describe penetration testing tools and the benefits to an organization
• Describe a deep dive into incident response techniques and tools
• Describe digital forensics and digital evidence.
• Discuss the power of scripting.

Crash Course on Python
This course is designed to teach you the foundations in order to write simple programs in Python using the most common structures. No previous exposure to programming is needed. By the end of this course, you'll understand the benefits of programming in IT roles; be able to write simple programs using Python; figure out how the building blocks of programming fit together; and combine all of this knowledge to solve a complex programming problem.
We'll start off by diving into the basics of writing a computer program. Along the way, you’ll get hands-on experience with programming concepts through interactive exercises and real-world examples. You’ll quickly start to see how computers can perform a multitude of tasks — you just have to write code that tells them what to do.

Ethical Hacking Essentials (EHE)
Ethical Hacking Essentials is an introductory cybersecurity course that covers ethical hacking and penetration testing fundamentals and prepares learners for a career in cybersecurity. This course will introduce learners to computer and network security concepts such as threats and vulnerabilities, password cracking, web application attacks, IoT and OT attacks, cloud computing, pentesting fundamentals, and more.
This course provides hands-on practical experience to learners thus giving them the skills necessary for a future in cybersecurity.
EHE-certified learners have an assured means of formal recognition to add to their resumes and show off their expertise and skills to prospective employers. This improves their prospects for employment advancement, higher salaries, and greater job satisfaction.

How to Use a Network Policy on Google Kubernetes Engine
This is a self-paced lab that takes place in the Google Cloud console. In this lab, you learn how to improve the security of your Kubernetes Engine by applying fine-grained restrictions to limit intra-cluster network communication.

App Development with Power Apps: Create Custom Components
Imagine having a rental company, in this case bike rental company, and having problems with managing the company's data. We can help you with that! You can make your life easier with no-code or low-code Power Apps capabilities.
In this guided project, we will create a SharePoint site and list that will contain data about all the bikes for rent owned by the company. Among other info, the bikes will also have the status Available or Unavailable for rent, so we can track them. After that we are going to create a Power Apps application and two custom components, a PopUp window and MenuNavigation, and we are going to add forms and a gallery so we can modify the bikes' status or add new bikes to the list, as well as to see all the bikes and their status in the app gallery.
The requirement for this project is having a Microsoft Developer Program account and you will be provided with instructions on how to acquire it.
Although anyone with basic understanding of data types, Excel-like formulas and variables can learn to use Power Apps, the recommended background for this guided project is being familiar with Power Platform. If you fit the criteria and would like to make your life easier by automating manual, time-consuming business tasks, then this project is for you! Let's get started!

Developing with Cloud Run
This is a self-paced lab that takes place in the Google Cloud console. This lab is based on the Serverless Toolbox episode “Using Python on Google Cloud with Cloud Run”. In this lab you will learn how to use Cloud Run.
Popular Internships and Jobs by Categories
Browse
© 2024 BoostGrad | All rights reserved


