Back to Courses





Information Technology Courses - Page 25
Showing results 241-250 of 1471

Containerization Using Docker
Welcome to "Containerization using Docker".
In this guided project you will learn how to use Docker to create a customised image of your application using Dockerfiles, enable data persistence and will also learn various methods to share your Docker images. Also, the task-based approach that we follow in our guided project will get you a better understanding of basic commands in Docker that comes very handy while working on your real-life project. . Most importantly you will leave this course with more confidence that will get you to work in Docker platform more efficiently.
If you have questions about course content, please post them in the forums to get help from others in the course community. For technical problems with the Coursera platform, visit the Learner Help Center.
Good luck as you get started, and I hope you enjoy the course!
Happy learning !!!!!

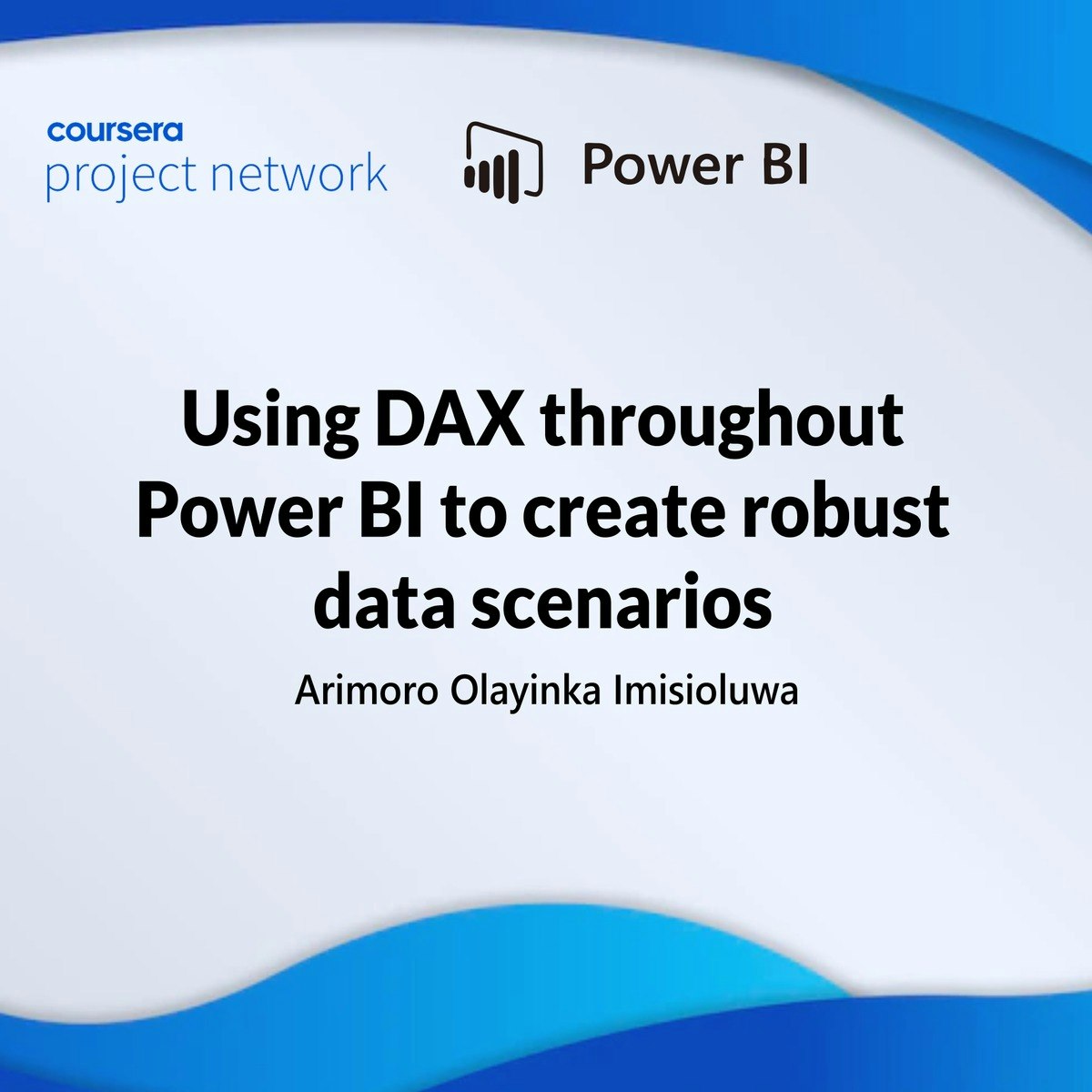
Using DAX throughout PowerBI to create robust data scenarios
If you don't use Data Analysis Expressions (DAX) Language, you will miss out on 95% of Power BI's potential as a fantastic analytical tool, and the journey to becoming a DAX master starts with the right step. This project-based course, "Using DAX throughout Power BI to create robust data scenarios," is intended for novice data analysts willing to advance their knowledge and skills.
This 2-hour project-based course will teach you how to create columns, measures, and tables using DAX codes while understanding the importance of context in DAX formulas. Finally, we'll round off the course by introducing time-intelligence functions and show you how to use Quick Measures to create complex DAX code. This course is structured in a systematic way and very practical, where you get an option to practice as you progress.
This project-based course is a beginner-level course in Power BI. Therefore, you should be familiar with the Power BI interface to get the most out of this project. Please join me on this beautiful ride! Let's take the first step in your DAX mastery journey!

Securing Software, Data and End Points
Course 4: Securing Software, Data and End Points
Welcome to Course Four. As we know, most attacks against systems involve exploiting vulnerabilities in software that powers hardware. Additionally, attackers may exploit vulnerabilities in the underlying hardware, especially when that hardware is for the protected against being stolen or accessed with unauthorized use, but their real target and all the tax is data. Therefore, it's so critical, the total set of software powering an organization's business logic and processes must be kept secure. As we'll see in this chapter, the software provides a layered environment. Building from a core or kernel of trustworthy functions up through to the mobile code and executable content. This enables and empowers all web apps and remote data access. Security professionals need to appreciate securing software covers two very different, but closely related major tasks. They need to ensure that the Security Posture of that software is known and understood, as well as ensure the software is installed, maintained, and used in ways consistent with Security Posture or improve it over time. As we discussed in the previous chapter, Security Posture is the set of risks, vulnerabilities controls, and residual risks pertaining to an asset or system. We summarize the safety or risk of using an asset and the degree of reliance that can be placed on the results from a specific context or situation. In this course, we'll build on that foundation by looking more closely at how the data can be the target of an attack and part of exploiting other vulnerabilities in the system. We'll explore what security professionals, as non-programmers, can do to reduce the risk of such malformed input attacks. In course two, we also discussed the non-human user concept as a general way to view management and security of devices and software entities to protect those entities from threats to their integrity and to protect the overall system and individual assets from unauthorized behavior by those non-human users. In this chapter, we'll build on those concepts, as we dive into Endpoint Security Issues and Approaches.
Course 4 Learning Objectives
After completing this course, the participant will be able to:
L4.1 - Discuss software systems and application security.
L4.2 - Recognize data security concepts and skills.
L4.3 - Identify malicious code and countermeasures.
L4.4 - Evaluate mobile device management (MDM) and security issues with mobile and autonomous endpoints.
L4.5 - Review attacks and countermeasures for virtual machines.
Course Agenda
Module 1: Securing Software (Domain 1 - Security Operations and Administration, Domain 3 - Risk Identification, Monitoring and Analysis , Domain 7 - Systems and Application Security )
Module 2: Securing Data (Domain 1 - Security Operations and Administration, Domain 7 - Systems and Application Security )
Module 3: Identify and Analyze Malicious Code and Activity (Domain 7 - Systems and Application Security)
Module 4: Implement and Operate Endpoint Security (Domain 7 - Systems and Application Security )
Module 5: Operate and Secure Virtual Environments (Domain 7 - Systems and Application Security , Domain 6 - Network and Communications Security)
Who Should Take This Course: Beginners
Experience Required: No prior experience required

Hands-on Introduction to Linux Commands and Shell Scripting
This course provides a practical introduction to Linux and commonly used Linux / UNIX shell commands. It teaches you the basics of Bash shell scripting to automate a variety of tasks. The course includes both video-based lectures as well as hands-on labs to practice and apply what you learn. You will have no-charge access to a virtual Linux server that you can access through your web browser, so you don't need to download and install anything to perform the labs.
You will learn how to interact with the Linux Terminal, execute commands, navigate directories, edit files, as well as install and update software.
You will work with general purpose commands like id, date, uname, ps, top, echo, man; directory management commands such as pwd, cd, mkdir, rmdir, find, df; file management commands like cat, wget, more, head, tail, cp, mv, touch, tar, zip, unzip; access control command chmod; text processing commands - wc, grep, tr; as well as networking commands - hostname, ping, ifconfig and curl.
You will create simple to more advanced shell scripts that involve Metacharacters, Quoting, Variables, Command substitution, I/O Redirection, Pipes & Filters, and Command line arguments. You will also schedule cron jobs using crontab.
This course is ideal for data engineers, data scientists, software developers, DevOps professionals, and cloud practitioners who want to get familiar with frequently used commands on Linux, MacOS and other Unix-like operating systems as well as get started with creating shell scripts.

Reliable Google Cloud Infrastructure: Design and Process
This course equips students to build highly reliable and efficient solutions on Google Cloud using proven design patterns. It is a continuation of the Architecting with Google Compute Engine or Architecting with Google Kubernetes Engine courses and assumes hands-on experience with the technologies covered in either of those courses. Through a combination of presentations, design activities, and hands-on labs, participants learn to define and balance business and technical requirements to design Google Cloud deployments that are highly reliable, highly available, secure, and cost-effective.

Dominant Risk Management Standards and Frameworks
Organizations with little experience in risk management will want to look to national and international organizations for guidance in designing and implementing their risk management efforts. There are two dominant organizations that offer guidance in this area: the U.S. National Institute for Standards in Technology (NIST) and the International Standards Organization.
This course examines the risk management frameworks and standards offered by these organization and then discusses other available approaches. The course concludes with a discussion of applications and tools to support the organization’s risk management effort.

Introduction to Test Driven Development (TDD)
Successful developers need to not only build the right software but build it right. To know your software works correctly, you need to test each unit of code. One of the best methods for this unit-level testing is test driven development.
This course provides a detailed overview of test driven development (TDD). First, you’ll learn what automated testing is and why it is essential for building robust applications resilient to failure. You’ll explore the basics of testing, including test cases, testing levels, and the traditional release cycle.
You’ll learn about TDD and its complement, behavior driven development (BDD): TDD tests individual units of code while BDD tests how these units work together.
Then you’ll examine TDD in detail. You’ll explore TDD’s benefits, concepts, and popular tools, and you’ll hone your new testing skills through hands-on labs. You’ll create TDD test cases by writing test assertions and building test fixtures, and you’ll run these test cases by using the Nose testing package. You’ll then practice more advanced TDD methods such as increasing code coverage, generating and using fake data, and testing mock objects.

Enterprise Database Migration
This course is intended to give architects, engineers, and developers the skills required to help enterprise customers architect, plan, execute, and test database migration projects. Through a combination of presentations, demos, and hands-on labs participants move databases to Google Cloud while taking advantage of various services.
This course covers how to move on-premises, enterprise databases like SQL Server to Google Cloud (Compute Engine and Cloud SQL) and Oracle to Google Cloud bare metal.

Maturing Risk Management
Course 8: Maturing Risk Management
In management science terms, maturing a process or practice means taking positive steps over time to make it more reliable, repeatable and efficient. In practice, this means getting better every day, while showing the measurements that demonstrate improvement and suggest other opportunities to improve. As we saw in chapters one and two risk management for information intensive organizations works best when using evidence-based reasoning to identify, characterize, and take actions as necessary to resolve the issues. Course eight will bring together numerous threads that are intrinsically related to managing the risks associated with information systems. Also, we know that cyber attack is a risk for all organizations. In this course, we will focus on bringing these ideas together in a context of continuous maturity modeling, measuring and monitoring. Risk alignment works best at the strategic long-term level of planning. By contrast risk maturation can be most effective when considered in day-to-day business operations. This is sometimes called operationalizing one's approach to risk management and maturation. Operationalizing risk management asks us to take the life cycle models about systems, software and data and connect or pivot them around business operations. We'll take on the view of the workers who use the business logic and the systems or the people who oversee the robotics and internet of things on the factory or warehouse floor and see how each of the different security disciplines brings something to them. This course has five modules. Module one focuses on change management and reveals how this detailed administratively intense process plays a primary role in protecting information systems. We'll also look at its vital contributions to incident response and remediation. Module two shows how physical security design principles are used to monitor and control the flow of physical objects in and out of various security zones. This module also considers the operational effects of safety planning and preparation on people and property, as well as availability and integrity of systems and information. Module three provides a different attitude and mindset about empowering and enabling the people in the organization to become more effective contributors and proponents of its information security. Security training programs have failed to help people complete their job safely and securely. New concepts such as micro chaining demonstrates that security education and awareness can add value to the security process. Module four shows us that system security assessment should be an ongoing task. Security has always involved continuous vigilance and integrity. Formal and informal audits demonstrate just how effective an organization's security controls are. As its process of maturing those controls continues to improve their performance. Module five brings many of these ideas and concepts together through business continuity and disaster recovery planning. The emphasis will be the operational support of these tasks, both in the planning and execution stages. We've prepared the foundations so you can bring concepts covered thus far into a cohesive daily operational context.
Course 8 Learning Objectives
After completing this course, the participant will be able to:
L8.1 - Identify operational aspects of change management.
L8.2 - Summarize physical security considerations.
L8.3 - Design a security education and awareness strategy.
L8.4 - Recognize common security assessment activities.
L8.5 - Classify the components of a business continuity plan and disaster recovery plan.
Course Agenda
Module 1: Participate in Change Management (Domain 1 - Security Operations and Administration)
Module 2: Physical Security Considerations (Domain 1 - Security Operations and Administration)
Module 3: Collaborate in Security Awareness and Training (Domain 1 - Security Operations and Administration)
Module 4: Perform Security Assessment Activities (Domain 3 - Risk Identification, Monitoring and Analysis)
Module 5: Understand and Support the Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP) (Domain 4 - Incident Response and Recovery)
Who Should Take This Course: Beginners
Experience Required: No prior experience required

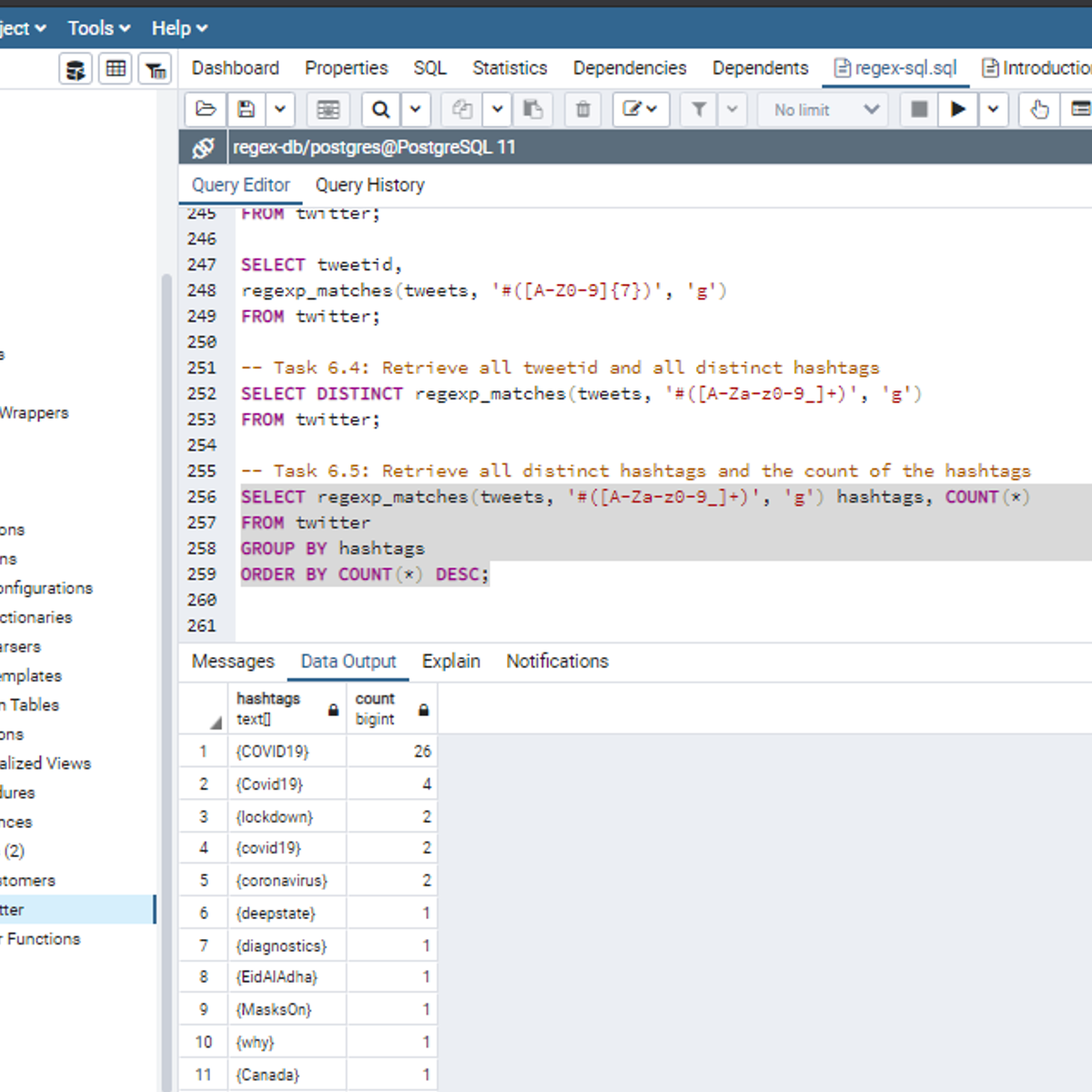
Introduction to Regular Expressions in SQL
Welcome to this project-based course, Introduction to Regular Expressions in SQL. In this project, you will learn how to use SQL regular expressions extensively for pattern matching to query tables in a database.
By the end of this 2-and-a-half-hour-long project, you will be able to use POSIX regular expressions together with meta (special) characters in the WHERE clause and the SELECT clause to retrieve the desired result from a database. In this project, we will move systematically by first revising the use of the LIKE and NOT LIKE operators in the WHERE clause. Then, we will use different regular expression metacharacters together with POSIX operators in the WHERE clause. Also, we will use regular expressions to work on tweets from Twitter data. Be assured that you will get your hands really dirty in this project because you will get to work on a lot of exercises to reinforce your knowledge of the concepts.
Also, for this hands-on project, we will use PostgreSQL as our preferred database management system (DBMS). Therefore, to complete this project, it is required that you have prior experience with using PostgreSQL. Similarly, this project is an intermediate SQL concept; so, a good foundation for writing SQL queries is vital to complete this project.
If you are not familiar with writing queries in SQL and want to learn these concepts, start with my previous guided projects titled “Querying Databases using SQL SELECT statement." I taught this guided project using PostgreSQL. So, taking these projects will give the needed requisite to complete this Introduction to Regular Expressions in SQL project. However, if you are comfortable writing queries in PostgreSQL, please join me on this wonderful ride! Let’s get our hands dirty!
Popular Internships and Jobs by Categories
Browse
© 2024 BoostGrad | All rights reserved


