Back to Courses







Computer Security And Networks Courses - Page 16
Showing results 151-160 of 277

Write your own Python tool to footprint a web application
In this 1-hour long project-based course, you will learn how to Learn basic functioning of a web application, Set up your private web Pentesting lab, Learn how to write python script to automatically footprint a web application.

Real-Time Cyber Threat Detection and Mitigation
This course introduces real-time cyber security techniques and methods in the context of the TCP/IP protocol suites. Explanation of some basic TCP/IP security hacks is used to introduce the need for network security solutions such as stateless and stateful firewalls. Learners will be introduced to the techniques used to design and configure firewall solutions such as packet filters and proxies to protect enterprise assets.
Perimeter solutions such as firewalls and intrusion prevention systems are shown to have significant drawbacks in common enterprise environments. The result of such weakness is shown to often exist as advanced persistent threats (APTs) from nation-state actors. Such attacks, as well as DDOS and third-party attacks, are shown to have potential solutions for modern enterprise.

Palo Alto Networks Cloud Security Fundamentals
In this Cloud Security Fundamentals course you will learn basic principles associated with securing the cloud and SaaS-based applications through Secure Access Service Edge architecture and identify concepts required to recognize and potentially mitigate attacks against traditional and hybrid datacenters as well as mission critical infrastructure. The course also demonstrates how to initially setup and configure containers on a docker bridge network and test the container security through the use of vulnerability scans and reports.

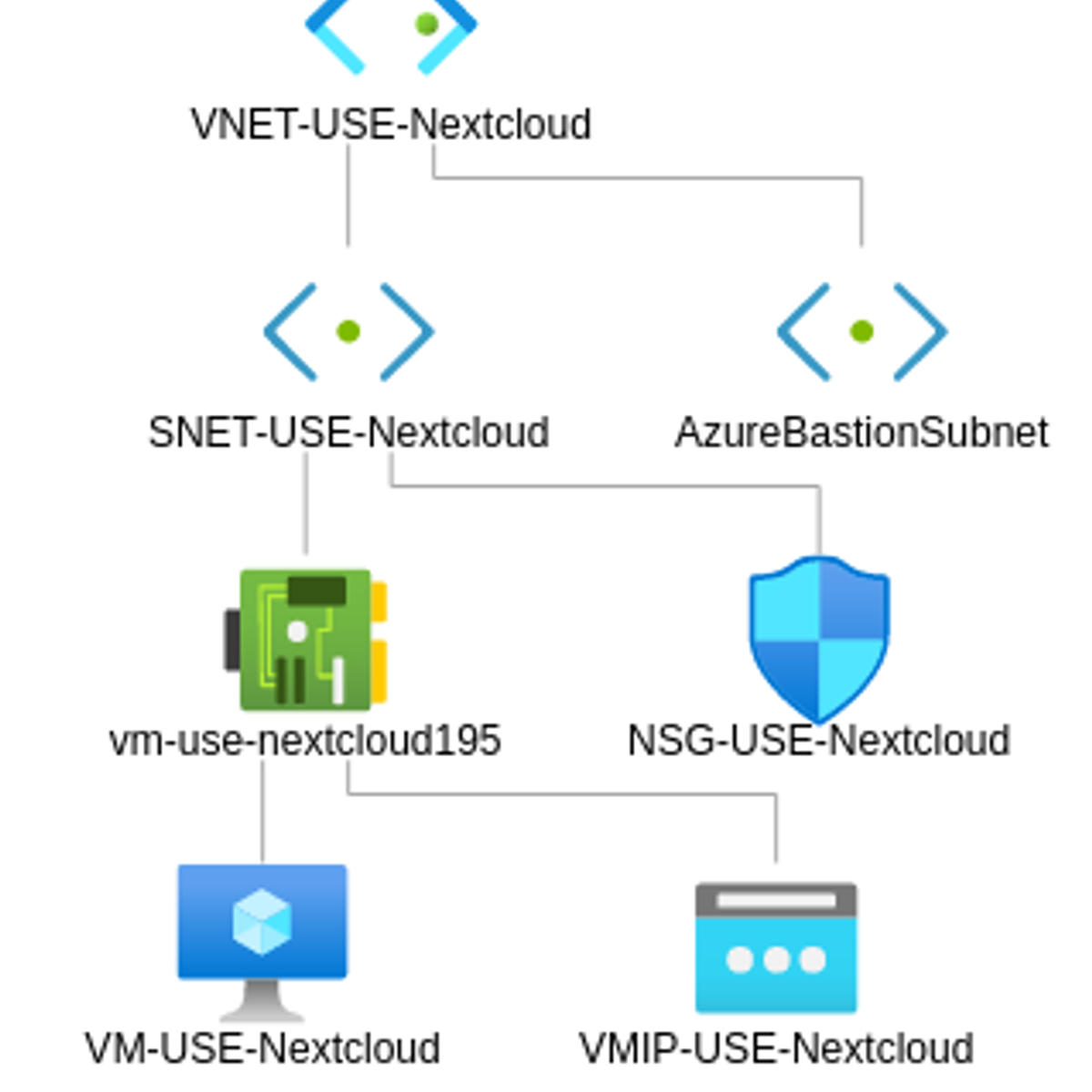
Azure: Create a Virtual Machine and Deploy a Web Server
In this Guided Project, you will create a Virtual Machine in Azure to deploy a web server, specifically a Nextcloud server. Instead of using just the presets, you will explore how the basic architecture of Azure works, by creating a Virtual Machine, connecting it to a subnet, protected by inbound and outbound rules thanks to Network Security Groups, in a Virtual Network. You'll also learn how to use Bastion to connect to the machine via SSH, without exposing an external port to the Internet, and then installing a simple Nextcloud server and make the Virtual Machine available to you by opening a public IP and a DNS label.
Note: before taking this Guided Project, if you don't have an Azure subscription yet, please create an Azure Free Trial beforehand at https://portal.azure.com

Security Principles
Welcome to course 1 of 5 of this Specialization, Security Principles.
After completing this course, the participant will be able to:
Discuss the foundational concepts of cybersecurity principles.
- Recognize foundational security concepts of information assurance.
- Define risk management terminology and summarize the process.
- Relate risk management to personal or professional practices.
- Classify types of security controls.
- Distinguish between policies, procedures, standards, regulations and laws.
- Demonstrate the relationship among governance elements.
- Analyze appropriate outcomes according to the canons of the (ISC)2 Code of Ethics when given examples.
- Practice the terminology and review security principles.
Agenda
Course Introduction
Module 1: Information Assurance
Module 2: Risk Management Process
Module 3: Security Controls
Module 4: Governance
Module 5: (ISC)2 Code of Ethics
Module 6: Course Summary
This training is for IT professionals, career changers, college students, recent college graduates, advanced high school students and recent high school graduates looking to start their path toward cybersecurity leadership by taking the Certified in Cybersecurity entry-level exam.
There are no prerequisites to take the training or the exam. It is recommended that candidates have basic Information Technology (IT) knowledge. No work experience in cybersecurity or formal education diploma/degree is required.

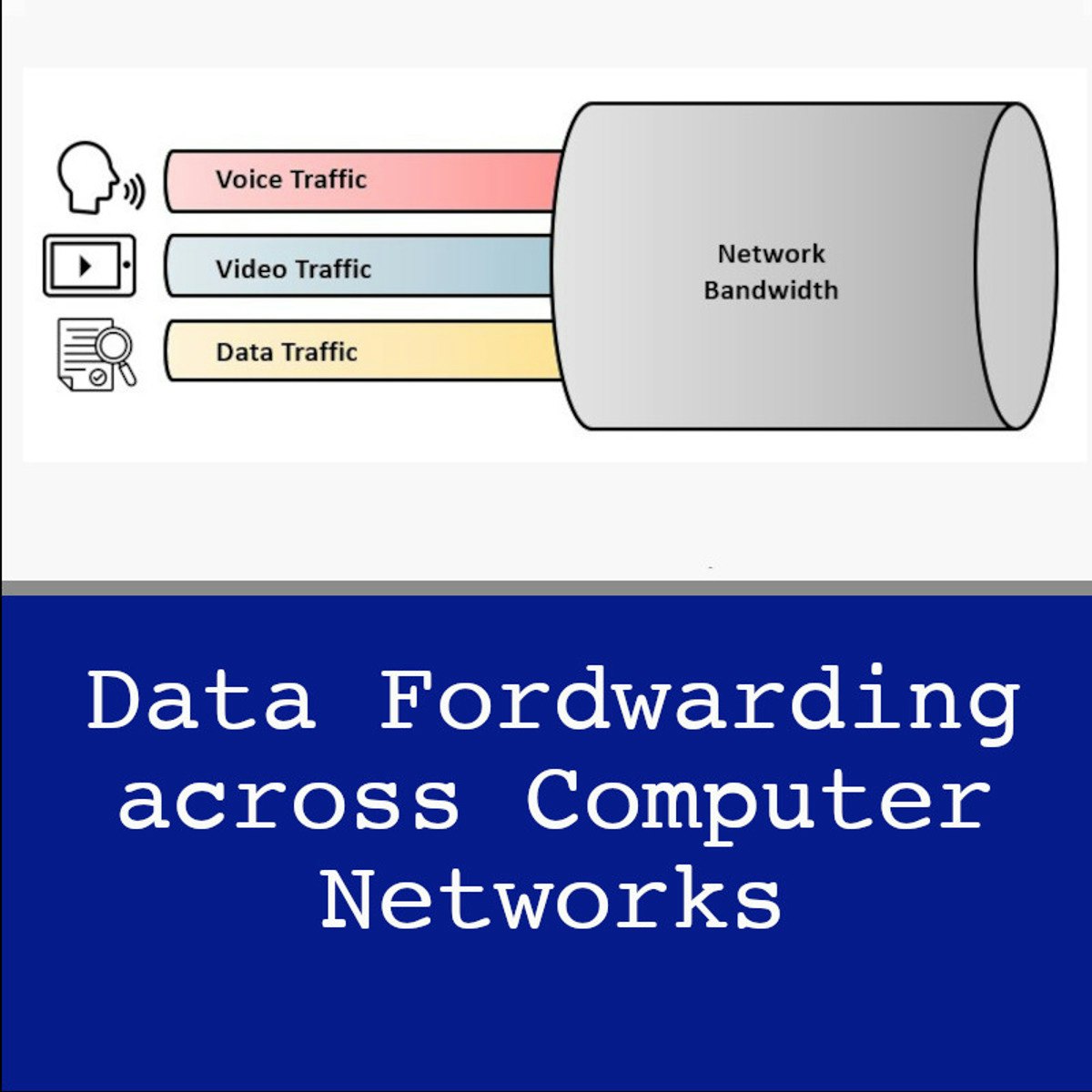
Data Forwarding Across Computer Networks
Welcome to the CCNA 1.3: Data Forwarding Across Computer Networks. This project is the third in the guided-projects series that is designed to help you acquire the hands-on skills required to pass the CCNA certification exam.
In this 2-hours guided project, you will understand how data is forwarded across computer networks, configure default and static routes on Cisco routers, set up dynamic routing using OSPF routing protocol, and verify and trace network routes.

Cyber Threats and Attack Vectors
Data breaches occur nearly every day. From very large retailers, down to your fantasy football website, and anywhere in between, they have been compromised in some way. How did the attackers get in? What did they do with the data they compromised? What should I be concerned with in my own business or my systems? This course is the second course in the Practical Computer Security. It will discuss types of threats and attack vectors commonly seen in today’s environment. I hate to be the bearer of bad news, but threats are all over the place! This course isn’t designed to insight fear that there is no hope for keeping systems and business secure, but rather educate you on how attacks are carried out so that you have a better sense of what to look out for in your business or with your systems.
Identifying, Monitoring, and Analyzing Risk and Incident Response and Recovery
Risk Identification, Monitoring, and Analysis: In the Risk Identification, Monitoring, and Analysis session, you will learn how to identify, measure, and control losses associated with adverse events. You will review, analyze, select, and evaluate safeguards for mitigating risk.You will learn processes for collecting information, providing methods of identifying security events, assigning priority levels, taking the appropriate actions, and reporting the findings to the correct individuals. After collection of the details from monitoring, we can analyze to determine if the system is being operated in accordance with accepted industry practices, and in compliance with organization policies and procedures.
Incident Response and Recovery: In the Incident Response and Recovery Session, you will gain an understanding of how to handle incidents using consistent, applied approaches in order to resolve. Once an incident is identified, action will be necessary in order to resolve. We will examine processes such as damage recovery, data integrity and preservation, and the collection, handling, reporting, and prevention. You will be introduced to the Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP) concepts and how they can be utilized in order to mitigate damages, recover business operations, and avoid critical business interruption. Through the use of the DRP, you will understand the procedures for emergency response and post-disaster recovery.
Course Objectives
1. Describe the risk management process
2. Perform security assessment activities
3. Describe processes for operating and maintaining monitoring systems
4. Identify events of interest
5. Describe the various source systems
6. Interpret reporting findings from monitoring results
7. Describe the incident handling process
8. Contribute to the incident handling process based upon role within the organization
9. Describe the supporting role in forensics investigation processes
10. Describe the supporting role in the business continuity planning process
11. Describe the supporting role in the disaster recovery planning process

Azure Infrastructure Fundamentals
Microsoft Azure is a service created by Microsoft to provide cloud computing for creating and managing applications and services using a cloud environment. Azure provides software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS). The platform supports many programming languages and frameworks and can be used alone or in a multi-vendor cloud environment.
This course focuses on the Fundamentals of Azure Infrastructure including infrastructure as a service. We’ll begin with understanding the subscription, configuring security and acquiring storage. Then you’ll build virtual machines and VNETS. Azure environments can be highly available and very resilient. Data can be backed up to the cloud for safety. These are the concepts we will discuss in this course.

Service Management with Linux
Service Management with Linux
Popular Internships and Jobs by Categories
Browse
© 2024 BoostGrad | All rights reserved


