Back to Courses








Computer Science Courses - Page 162
Showing results 1611-1620 of 2309

Cybersecurity Policy for Water and Electricity Infrastructures
This course will examine the drinking water and electricity infrastructures, and various policies that have been developed to help guide and strengthen their cybersecurity programs. The drinking water and electricity infrastructures are two of fourteen subsectors comprising what are known as "lifeline infrastructure". The 2013 National Infrastructure Protection Plan identifies four lifeline infrastructure sectors: 1) water, 2) energy, 3) transportation, and 4) communications. These sectors are designated "lifeline" because many other infrastructures depend upon them. The drinking water subsector is part of the water sector, and the electricity subsector is part of the energy sector. Both subsectors are overseen by the Department of Homeland Security National Protection and Programs Directorate which manages the DHS National Infrastructure Protection Program. The NIPP employs a five-step continuous improvement program called the Risk Management Framework. NIPP implementation is overseen by DHS-designated Sector-Specific Agencies staffed by various Federal departments. The Sector-Specific Agencies work in voluntary cooperation with industry representatives to apply the Risk Management Framework and document results in corresponding Sector-Specific Plans. The program began in 2007 and the most recent Sector-Specific Plans were published in 2016. In February 2013, President Obama issued Executive 13636 directing the National Institute of Standards and Technology to develop a voluntary set of recommendations for strengthening infrastructure cybersecurity measures. EO13636 also asked Federal agencies with regulating authority to make a recommendation whether the NIST Cybersecurity Framework should be made mandatory. The Environmental Protection Agency who is both the SSA and regulatory authority for the drinking water subsector recommended voluntary application of the NIST Cybersecurity Framework. The Department of Energy who is both the SSA and regulatory authority for the electricity subsector replied that it was already implementing the Electricity Subsector Cybersecurity Capability Maturity Model, which indeed was what the NIST Cybersecurity Framework was based on. The Department of Energy, though, recommended voluntary application of the ES-C2M2. This module will examine both the drinking water and electricity lifeline infrastructure subsectors, and elements and application of the NIST Cybersecurity Framework and ES-C2M2.

Building Regression Models with Linear Algebra
In this course, you'll learn how to distinguish between the different types of regression models. You will apply the Method of Least Squares to a dataset by hand and using Python. In addition, you will learn how to employ a linear regression model to identify scenarios. Let's get started!

Azure Data Factory : Implement SCD Type 1
In this project, you will learn how to implement one of the most common concept in real world projects i.e. Slowly Changing Dimension Type 1, using Azure Data Factory.
Pre-requisites:
Azure subscription
Azure Data Factory knowledge (Basic)
Following are the tasks covered in this project:
Task 1: Understand Slowly Changing Dimension (SCD) Type 1
In this task, we will try to understand the concept of Slowly Changing Dimension and its different types, but will focus on Type 1 using a simple example.
Task 2: Create Azure services like Azure Data Factory, Azure SQL Database
In this task, we are going to create the azure services like azure data factory and azure sql database which are going to be used in later tasks. Azure sql database is going to contain the staging and dimension table whereas azure data factory is going to be used to create the data pipeline
Task 3: Create Staging and Dimension Table in Azure SQL Database
In this task, we will create the staging and dimension table in azure sql database. Also, we will insert some dummy records in staging table
Task 4: Create a ADF pipeline to implement SCD Type 1 (Insert Logic)
In this task, we are going to create the pipeline in azure data factory and implement the logic to insert new records which exists in staging table but doesnt exist in dimension. This is one scenario/use case of SCD Type 1.
Task 5: Create a ADF pipeline to implement SCD Type 1 (Update Logic)
In this task, we are going to create the pipeline in azure data factory and implement the logic to update records which exists in staging table as well as in dimension. This is another use case/scenario of SCD Type 1
Task 6: Demo of ADF pipeline
This is final task in which we will run the pipeline to see whether it satisfies both the use case/scenario of SCD Type 1
All the Best !!

Configuring the C/C++ Extension Pack with Visual Studio Code
In this 1.5 hours guided project, you will learn how to install, configure and use the C/C++ extension pack in Visual Studio Code. At the end of the class, you will be familiar with the major components of the extension pack. You will also be able to build, debug, customize your development experience, and distribute your configurations to other workstations. Topics include C++ colorization, Intellisense, build, debug, CMake tools, SSH remote development, and Doxygen documentation generator. Basic C or C++ programming experience is highly recommended.

User Authentication: Identity-Aware Proxy
This is a self-paced lab that takes place in the Google Cloud console. Learn how to restrict access selected authenticated users with Identity-Aware Proxy without special programming. Discover how to retrieve user identity information from IAP.
Cryptography I
Cryptography is an indispensable tool for protecting information in computer systems. In this course you will learn the inner workings of cryptographic systems and how to correctly use them in real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two parties generate a shared secret key. Throughout the course participants will be exposed to many exciting open problems in the field and work on fun (optional) programming projects. In a second course (Crypto II) we will cover more advanced cryptographic tasks such as zero-knowledge, privacy mechanisms, and other forms of encryption.

Creative Programming for Digital Media & Mobile Apps
This course is for anyone who would like to apply their technical skills to creative work ranging from video games to art installations to interactive music, and also for artists who would like to use programming in their artistic practice.
This course will teach you how to develop and apply programming skills to creative work. This is an important skill within the development of creative mobile applications, digital music and video games. It will teach the technical skills needed to write software that make use of images, audio and graphics, and will concentrate on the application of these skills to creative projects. Additional resources will be provided for students with no programming background.
At the end of this course, you will be able to:
* Write creative, audiovisual programs in the Processing environment that run on desktop and mobile
* Programatically manipulate sound in creative ways
* Display images and image sequences
* Generate interactive, algorithmic graphics
* Work with a 2D physics engine to create a basic game

Operations Research (1): Models and Applications
Operations Research (OR) is a field in which people use mathematical and engineering methods to study optimization problems in Business and Management, Economics, Computer Science, Civil Engineering, Industrial Engineering, etc. This course introduces frameworks and ideas about various types of optimization problems in the business world. In particular, we focus on how to formulate real business problems into mathematical models that can be solved by computers.

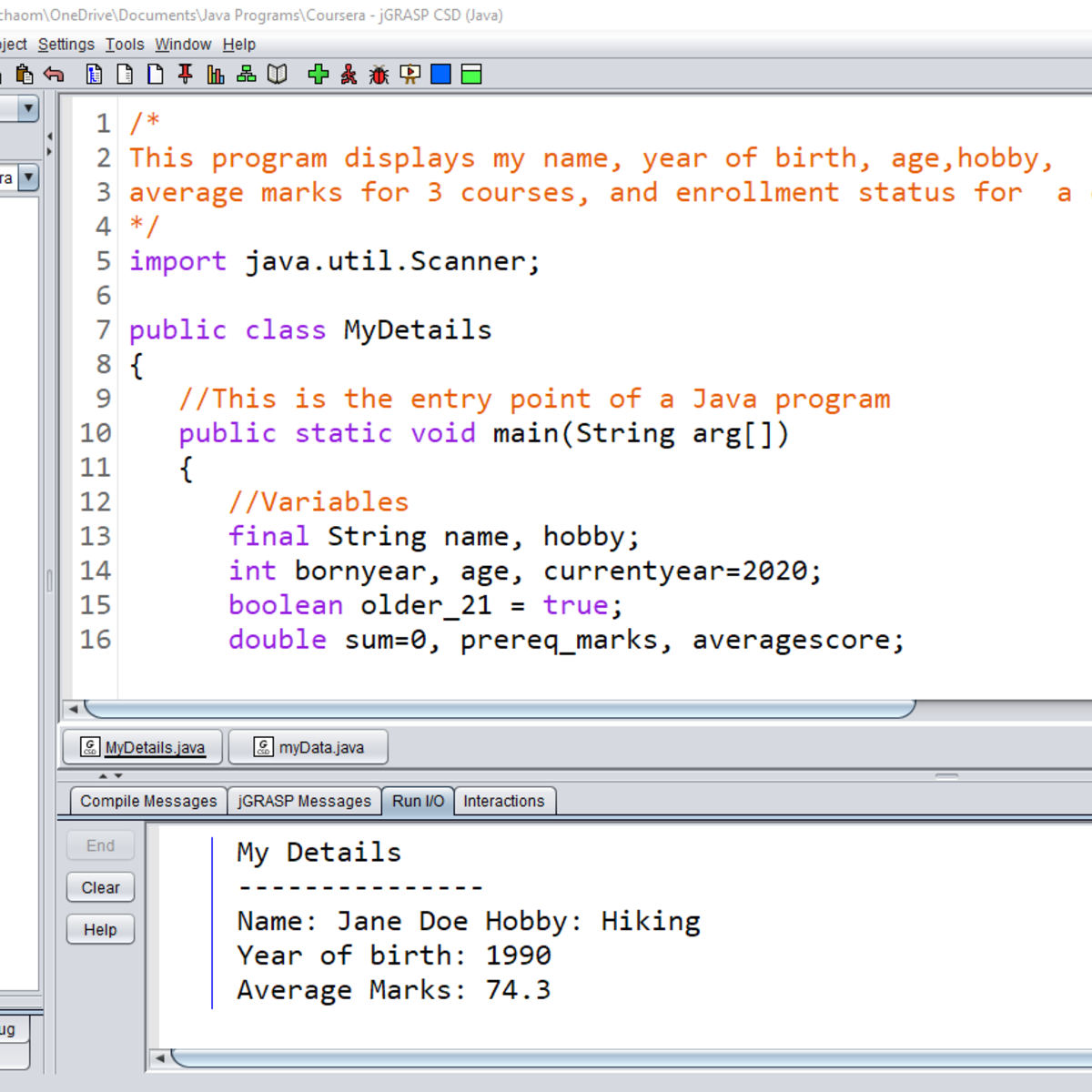
Create your first Java project using jGRASP
This project provides a step-by-step approach in instruction and will equip you with fundamental concepts of Java programming from the ground up. Using jGRASP development environment, you will create a program that processes details that are a prerequisite for a course you would like to enroll in. These details are your name, year of birth, age, hobby, and the average score from three prerequisite courses. To be enrolled for the course, you have to be older than 21 and you should also have attained a mark of at least 50 in each of the three previous courses. By creating this project, you will master the concepts of using a class, comments, variables, input, output, operators, and control flow in Java programming.
If you are a beginner and this is your first course in Java programming you will benefit from writing a program from a blank sheet to a fully functioning program. If you already have programming experience, this is an opportunity to refresh your skills in Java programming by going back to basics. No matter your level, you will be able to apply the skills obtained from this course in real-life programming exercises. To provide you with support outside the course, you will find a pool of additional notes and exercises that you can try at home.
If you ever wanted to become better at computer programming using Java by building on your fundamental skills, this project is the right place to start!

Programming Languages Ⅱ
The goal of this course is to help students:
1. learn new languages quickly,
2. evaluate various languages and pick the most suitable one for a given task,
3. know when and how to design a little language, and
4. understand the effects of languages on thought and communication.
We will study programming language concepts, not as paradigms but as a set of basic building blocks, by 1) implementing interpreters for the concepts using the Scala programming language and 2) rigorously discussing the concepts using the operational semantics.
