Back to Courses







Information Technology Courses - Page 11
Showing results 101-110 of 1471

Reduce Costs for the Managed Service for Prometheus
This is a self-paced lab that takes place in the Google Cloud console.
In this lab, you will explore cost control mechanisms when utilizing the Managed Service for Prometheus on Google Cloud. The Google Cloud Managed Service for Prometheus charges for the number of samples ingested into Cloud Monitoring and for read requests to the Monitoring API. The number of samples ingested is the primary contributor to your cost.

Kubernetes in AWS: Create Cluster in EKS in your own VPC
Kubernetes in AWS: Create Cluster in EKS in your own VPC
IMPORTANT: You must have or create an AWS account to work along to this course.
By the end of this course, you will know the steps necessary to set up your own EKS clusters in AWS. You will configure the AWS CLI and connect your local kubectl to the cluster so you can perform direct operations to the cluster.

Wire Up an Auction Website with GraphQL
In this 1.5 hours class, you will get up to speed with GraphQL, a popular query language that is used by many companies including Facebook, and right here at Coursera! GraphQL provides a standardized and flexible way to structure queries and exchange data among various database and server platforms. We will focus on the syntax and the fundamentals like data types, arguments, aliases, fragments, directives, and mutations. By the end of this class, you will have wired up a mock auction website with a GraphQL server and made it functional! Javascript and REST API are required as prerequisites.

Introduction to Cybersecurity for Business
The world runs computers. From small to large businesses, from the CEO down to level 1 support staff, everyone uses computers. This course is designed to give you a practical perspective on computer security. This course approaches computer security in a way that anyone can understand. Ever wonder how your bank website is secure when you connect to it? Wonder how other business owners secure their network? Wonder how large data breaches happen? This is practical computer security. It will help you answer the question – what should I focus on?

Aruba Network Automation Basics
Aruba networking technologies are purpose-built with automation in mind to meet the increasing demands on IT’s ability to achieve business outcomes more efficiently. In Aruba Network Automation Basics you'll get an introduction to network automation concepts, key automation tools including Python
and Ansible, and how to apply network automation in practice with Aruba products. This course is great for the networking professionals who want an introduction to the world of coding, scripting, and automation.

Teaching with Google Classroom
This is a self-paced lab that takes place in the Google Cloud console.
As a teacher with Google Workspace for Education, use Google Classroom to set up a class; set up communication with Gmail and Google Meet through the class page; create assignments; and use Calendar to keep the class on schedule and students aware of deadlines.

Understanding and Analyzing Your Costs with Google Cloud Billing Reports
This is a self-paced lab that takes place in the Google Cloud console. In this lab, you familiarize yourself with Google Cloud Billing reports, which provides built-in cost reporting for GCP within the Google Cloud Console. You view Billing reports from a live billing account, understand current and forecasted GCP costs, and then analyze costs using report filters to identify cost drivers and trends

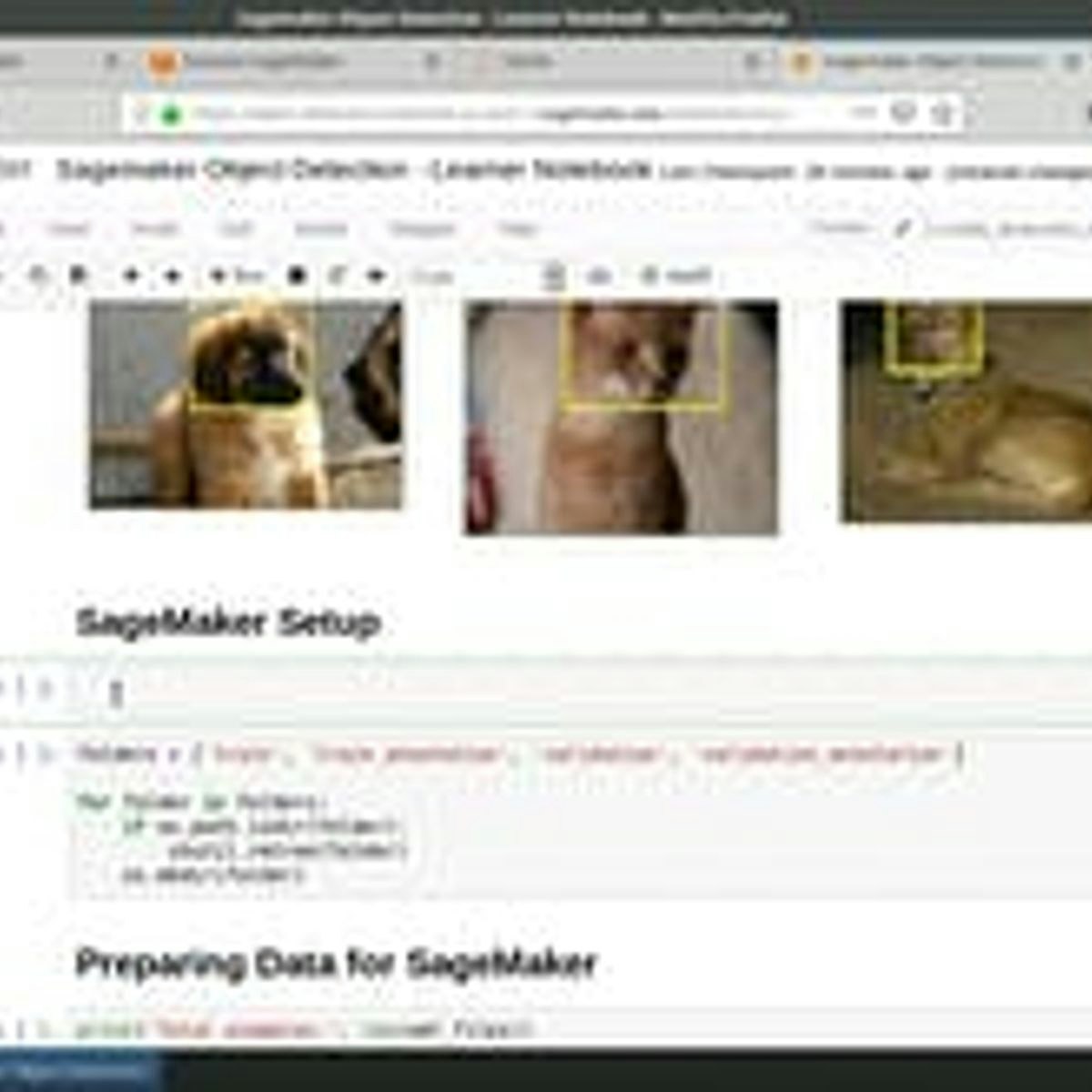
Object Detection with Amazon Sagemaker
Please note: You will need an AWS account to complete this course. Your AWS account will be charged as per your usage. Please make sure that you are able to access Sagemaker within your AWS account. If your AWS account is new, you may need to ask AWS support for access to certain resources. You should be familiar with python programming, and AWS before starting this hands on project. We use a Sagemaker P type instance in this project, and if you don't have access to this instance type, please contact AWS support and request access.
In this 2-hour long project-based course, you will learn how to train and deploy an object detector using Amazon Sagemaker. Sagemaker provides a number of machine learning algorithms ready to be used for solving a number of tasks. We will use the SSD Object Detection algorithm from Sagemaker to create, train and deploy a model that will be able to localize faces of dogs and cats from the popular IIIT-Oxford Pets Dataset.
Since this is a practical, project-based course, we will not dive in the theory behind deep learning based SSD or Object Detection, but will focus purely on training and deploying a model with Sagemaker. You will also need to have some experience with Amazon Web Services (AWS).
Note: This course works best for learners who are based in the North America region. We’re currently working on providing the same experience in other regions.

IAM Role Revoking and Permissions Boundary
By the end of this Project, you will be able to learn how and when to revoke an IAM Role. In this scenario, we are going to deal with a real time example. Suppose, you are working as a security analyst with a global organization called "XYZ". You assigned an IAM role to an EC2 instance and the temporary credentials generated by the role assumption got leaked to a third party. Lets see how can we deal with this situation in an ideal way. This project also reviews the functionality provided by Permission Boundaries and looks at a common use case permission delegation. After completing this Project, you will get a detailed idea of Role Revoking and Permission Boundary.

Palo Alto Networks: VM-Series Advanced Deployment
This is a self-paced lab that takes place in the Google Cloud console. In this lab you will use Terraform to deploy 2 VM-Series firewalls that secure ingress/egress traffic from 2 spoke VPCs, using internal load balancers as next hop.
Popular Internships and Jobs by Categories
Find Jobs & Internships
Browse
© 2024 BoostGrad | All rights reserved