Back to Courses






Computer Security And Networks Courses - Page 9
Showing results 81-90 of 277

Securing Google Cloud with CFT Scorecard
This is a self-paced lab that takes place in the Google Cloud console. CFT Scorecard is a utility you can combine with Forseti policies to check for violations in your Google Cloud environment.

Homeland Security & Cybersecurity Connection - It's Not About the Terrorists
Welcome to Course 1 in CS4950, Homeland Security and Cybersecruity. In this course we examine the origins of homeland security and its connection with cybersecurity. Homeland security is about safeguarding the United States from domestic catastrophic destruction. Catastrophic destruction comes in two forms: natural and man-made. For most of history the man-made variety came in the form of warfare and required the combined resources of a nation state. All that changed March 20th, 1995. On that date, members of a quasi-religious cult in Japan attacked the Tokyo subway system using Sarin gas. It was the first deployment of a weapon of mass destruction my a non-state actor. The power of destruction once reserved to nation states was now available to small groups, even individuals. The incident was a wake up call for governments around the world. Defense establishments designed to keep rogue states in check were practically useless against non-state actors. Overnight, the number of potential enemies multiplied a hundred, maybe even a thousand-fold. In response to the Tokyo Subway Attacks, the United States took measures to protect itself from WMD attack by non-state actors. Those measures were still being enacted when the nation was attacked on 9/11. On September 11, 2001, nineteen hijackers inflicted as much damage as the Imperial Japanese Navy on December 7, 1941. The investigating 9/11 Commission noted the attacks for their "surpassing disproportion". The hijackers had achieved WMD effects without using WMD. They did this by subverting the nation's transportation infrastructure, turning passenger jets into guided missiles. Again, the security implications were profound. Non-state actors seeking to inflict domestic catastrophic destruction did not need to import, fabricate, or acquire WMD as the nation was surrounded by the means of its own destruction in the form of critical infrastructure. The vulnerability of critical infrastructure had not gone unnoticed. Again, in response to the Tokyo Subway attacks, which themselves had been an attack on Japanese infrastructure, President Clinton in 1996 commissioned a panel to investigate the threat to United States' infrastructure. The panel replied in 1997 that there was no immediate threat to US infrastructure, but they were concerned with the growing risk of cyber attack. The same cyber physical systems that fueled the explosive growth of the Internet were being incorporated into Industrial Control Systems that underpinned much of the nation's critical infrastructure. The panel noted that the knowledge and skills necessary to mount a cyber attack on the nation's infrastructure was growing. As a result of this observation, President Clinton in 1998 ordered the protection of US critical infrastructure, especially from cyber attack. Following 9/11, critical infrastructure protection and cybersecurity were designated core missions in the 2002 Homeland Security Act establishing the new Department of Homeland Security. They remain core missions to this day, but many don't see the connection. The connection is this: cybersecurity is essential to critical infrastructure protection, which is essential to homeland security, which is about safeguarding the United States from domestic catastrophic destruction. I look forward to working with you in the coming lessons. Best wishes and good luck!
Course 1: Homeland Security & Cybersecurity Connection
Course 2: Cybersecurity Policy for Water and Electricity Infrastructures
Course 3: Cybersecurity Policy for Aviation and Internet Infrastructures
Course 4: Homeland Security & Cybersecurity Future

Architecting with Google Kubernetes Engine: Production
In this course, "Architecting with Google Kubernetes Engine: Production," you'll learn about Kubernetes and Google Kubernetes Engine (GKE) security; logging and monitoring; and using Google Cloud managed storage and database services from within GKE.
This is the final course of the Architecting with Google Kubernetes Engine series. After completing this course, enroll in the Reliable Google Cloud Infrastructure: Design and Process course or the Hybrid Cloud Infrastructure Foundations with Anthos course.

Cloud Application Security
After completing the course, the student should be able to do the following:
● List and describe the OWASP Top 10 vulnerabilities.
● Identify methods to provide cloud security assurance as part of the development life cycle, e.g. in a continuous delivery environment.
● List and describe the different types of virtualization or sandboxing used to protect cloud applications at either the server or client.
● Describe the application of authentication factors and federated identity solutions in cloud client and server authentication.
● Given a cloud application, explain where and how the necessary crypto keys, passwords, and other security secrets should be stored and distributed.

Introduction to Automated Analysis
This course introduces state-of-the-art techniques for automated analysis. Automated analysis encompasses both approaches to automatically generate a very large number of tests to check whether programs meet requirements, and also means by which it is possible to *prove* that software meets requirements and that it is free from certain commonly-occurring defects, such as divide-by-zero, overflow/underflow, deadlock, race-condition freedom, buffer/array overflow, uncaught exceptions, and several other commonly-occurring bugs that can lead to program failures or security problems. The learner will become familiar with the fundamental theory and applications of such approaches, and apply a variety of automated analysis techniques on example programs.
After completing this course, a learner will be able to:
- Understand the foundations of automated verification: randomization and symbolic representations
- Distinguish the strengths and weaknesses of random testing, symbolic analysis, static analysis, and model checking
- Use a variety of state-of-the-art static analysis and automated testing tools for automated verification
- Create executable requirements as an oracle suitable for automated testing and symbolic analysis
- Understand how the choice of oracle affects fault-finding for automated analysis strategies.
- Use automated testing to achieve full mutation coverage
- Create a test plan that utilizes both manually-written tests and automated tests towards maximizing rigor, minimizing effort and time, and minimizing test costs.
This course is intended for learners interested in understanding the principles of automation and the application of tools
for analysis and testing of software This knowledge would benefit several typical roles: Software Engineer, Software Engineer in Test, Test Automation Engineer, DevOps Engineer, Software Developer, Programmer, Computer Enthusiast. We expect that you have some familiarity with the Software development Life-Cycle, an understanding of the fundamentals of software testing, similar to what is covered in the Introduction to Software Testing and Black-box and White-Box Testing Courses.
Familiarity with an object-oriented language such as Java or ability to pick-up Java syntax quickly to write and modify code, and willingness to use tools and IDEs are assumed.

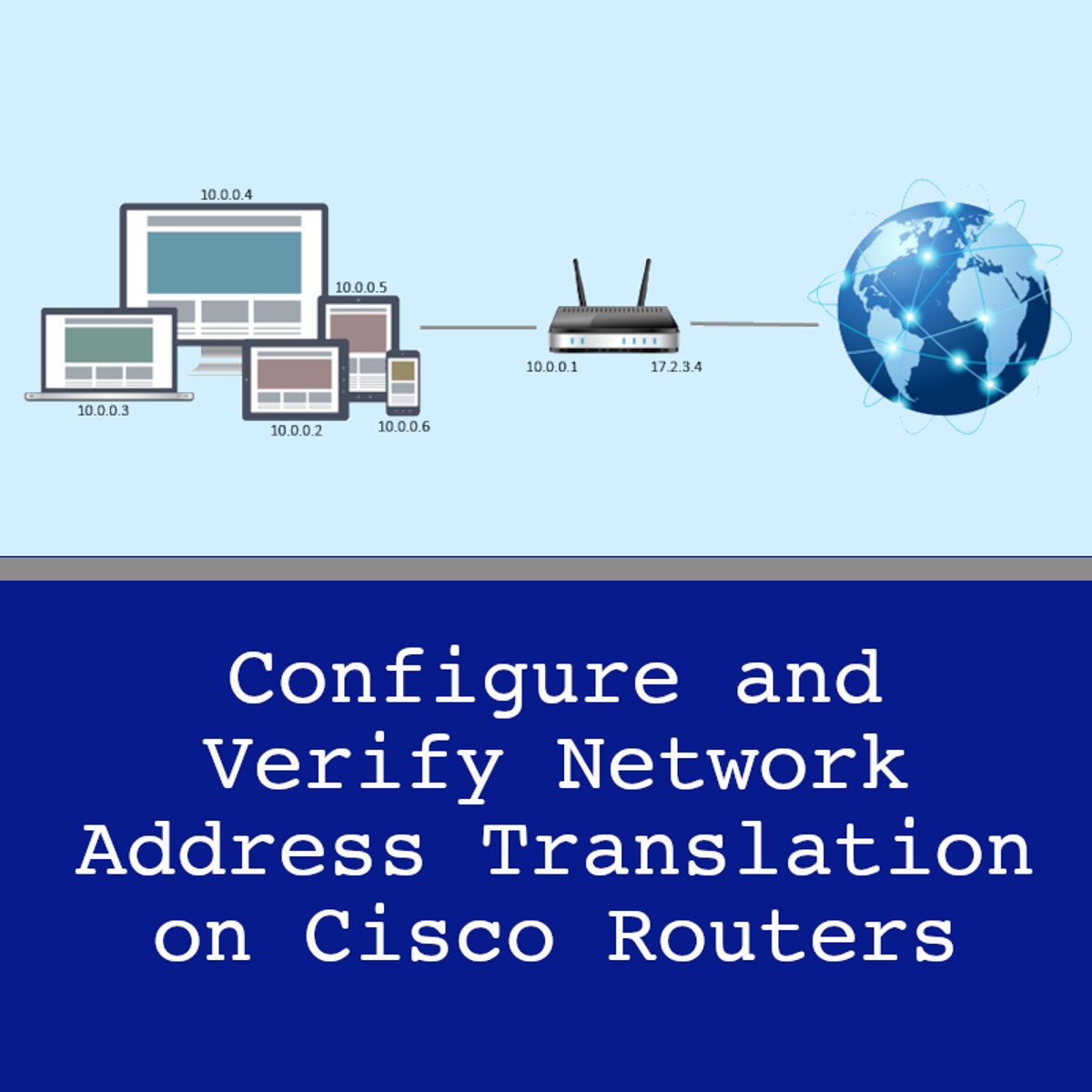
Configure and Verify NAT on Cisco routers
Welcome to the CCNA 1.9: Configure and Verify NAT on Cisco routers. This project is the ninth in a CCNA learning series that is designed to help you acquire the hands-on skills required to pass the CCNA certification exam.
In this 2-hour guided project, you will configure static and dynamic Network Address Translation (NAT) on Cisco routers, you will also setup NAT overloading with Port Address Translation (PAT), and verify NAT configuration on Cisco routers.

Peer-to-Peer Protocols and Local Area Networks
In this course, we discuss peer-to-peer protocols and local area networks. Part one in this course is to answer the question of how does a peer-to-peer protocol deliver reliable data transfer service across unreliable transmission lines or networks. We focus on several medium access control protocols and their performance analysis. In the second part, we discuss how medium access control protocols coordinate the access to the communication channel so that information gets through from a source to a destination in the same broadcast local area network. We further discuss local area network and wireless LAN.

Managing Cybersecurity Incidents and Disasters
Most organizations plan for routine operations, but what happens when unexpected events overtake the routine? This course examines contingency planning used to prepare for and manage non-normal operations, including cybersecurity incidents – like hacking attempts, web site defacement, denial of service attacks, information disclosures; a well as other natural and man-made cybersecurity disasters.
In this course, a learner will be able to:
● Define and describe the components of a cybersecurity contingency planning program
● Identify the components and structure of an effective cybersecurity incident response program
● Identify the components and structure of an effective cybersecurity disaster recovery program
● Define and describe recommended contingency strategies including data backup and recovery and continuity of cybersecurity operations.

Aruba Mobility Basics
In Aruba Mobility Basics, you will learn how Radio Frequency (RF) works! You will compare the differences between a wired and a wireless network, identify WLAN organizations that set Wi-Fi standards and the basics of radio communication. This course introduces you to what goes into setting up a wireless network and how wireless functions at a basic level without requiring any technical experience. Typical candidates for this course are individuals who are new to networking and want to learn the basics of wireless networking.

Hacking and Patching
In this MOOC, you will learn how to hack web apps with command injection vulnerabilities in a web site of your AWS Linux instance. You will learn how to search valuable information on a typical Linux systems with LAMP services, and deposit and hide Trojans for future exploitation. You will learn how to patch these web apps with input validation using regular expression. You will learn a security design pattern to avoid introducing injection vulnerabilities by input validation and replacing generic system calls with specific function calls. You will learn how to hack web apps with SQL injection vulnerabilities and retrieve user profile information and passwords. You will learn how to patch them with input validation and SQL parameter binding. You will learn the hacking methodology, Nessus tool for scanning vulnerabilities, Kali Linux for penetration testing, and Metasploit Framework for gaining access to vulnerable Windows Systems, deploying keylogger, and perform Remote VNC server injection. You will learn security in memory systems and virtual memory layout, and understand buffer overflow attacks and their defenses. You will learn how to clone a Kali instance with AWS P2 GPU support and perform hashcat password cracking using dictionary attacks and known pattern mask attacks.
Popular Internships and Jobs by Categories
Browse
© 2024 BoostGrad | All rights reserved


