Back to Courses







Computer Security And Networks Courses - Page 5
Showing results 41-50 of 277

Securing Software, Data and End Points
Course 4: Securing Software, Data and End Points
Welcome to Course Four. As we know, most attacks against systems involve exploiting vulnerabilities in software that powers hardware. Additionally, attackers may exploit vulnerabilities in the underlying hardware, especially when that hardware is for the protected against being stolen or accessed with unauthorized use, but their real target and all the tax is data. Therefore, it's so critical, the total set of software powering an organization's business logic and processes must be kept secure. As we'll see in this chapter, the software provides a layered environment. Building from a core or kernel of trustworthy functions up through to the mobile code and executable content. This enables and empowers all web apps and remote data access. Security professionals need to appreciate securing software covers two very different, but closely related major tasks. They need to ensure that the Security Posture of that software is known and understood, as well as ensure the software is installed, maintained, and used in ways consistent with Security Posture or improve it over time. As we discussed in the previous chapter, Security Posture is the set of risks, vulnerabilities controls, and residual risks pertaining to an asset or system. We summarize the safety or risk of using an asset and the degree of reliance that can be placed on the results from a specific context or situation. In this course, we'll build on that foundation by looking more closely at how the data can be the target of an attack and part of exploiting other vulnerabilities in the system. We'll explore what security professionals, as non-programmers, can do to reduce the risk of such malformed input attacks. In course two, we also discussed the non-human user concept as a general way to view management and security of devices and software entities to protect those entities from threats to their integrity and to protect the overall system and individual assets from unauthorized behavior by those non-human users. In this chapter, we'll build on those concepts, as we dive into Endpoint Security Issues and Approaches.
Course 4 Learning Objectives
After completing this course, the participant will be able to:
L4.1 - Discuss software systems and application security.
L4.2 - Recognize data security concepts and skills.
L4.3 - Identify malicious code and countermeasures.
L4.4 - Evaluate mobile device management (MDM) and security issues with mobile and autonomous endpoints.
L4.5 - Review attacks and countermeasures for virtual machines.
Course Agenda
Module 1: Securing Software (Domain 1 - Security Operations and Administration, Domain 3 - Risk Identification, Monitoring and Analysis , Domain 7 - Systems and Application Security )
Module 2: Securing Data (Domain 1 - Security Operations and Administration, Domain 7 - Systems and Application Security )
Module 3: Identify and Analyze Malicious Code and Activity (Domain 7 - Systems and Application Security)
Module 4: Implement and Operate Endpoint Security (Domain 7 - Systems and Application Security )
Module 5: Operate and Secure Virtual Environments (Domain 7 - Systems and Application Security , Domain 6 - Network and Communications Security)
Who Should Take This Course: Beginners
Experience Required: No prior experience required

Reliable Google Cloud Infrastructure: Design and Process
This course equips students to build highly reliable and efficient solutions on Google Cloud using proven design patterns. It is a continuation of the Architecting with Google Compute Engine or Architecting with Google Kubernetes Engine courses and assumes hands-on experience with the technologies covered in either of those courses. Through a combination of presentations, design activities, and hands-on labs, participants learn to define and balance business and technical requirements to design Google Cloud deployments that are highly reliable, highly available, secure, and cost-effective.

Dominant Risk Management Standards and Frameworks
Organizations with little experience in risk management will want to look to national and international organizations for guidance in designing and implementing their risk management efforts. There are two dominant organizations that offer guidance in this area: the U.S. National Institute for Standards in Technology (NIST) and the International Standards Organization.
This course examines the risk management frameworks and standards offered by these organization and then discusses other available approaches. The course concludes with a discussion of applications and tools to support the organization’s risk management effort.

Maturing Risk Management
Course 8: Maturing Risk Management
In management science terms, maturing a process or practice means taking positive steps over time to make it more reliable, repeatable and efficient. In practice, this means getting better every day, while showing the measurements that demonstrate improvement and suggest other opportunities to improve. As we saw in chapters one and two risk management for information intensive organizations works best when using evidence-based reasoning to identify, characterize, and take actions as necessary to resolve the issues. Course eight will bring together numerous threads that are intrinsically related to managing the risks associated with information systems. Also, we know that cyber attack is a risk for all organizations. In this course, we will focus on bringing these ideas together in a context of continuous maturity modeling, measuring and monitoring. Risk alignment works best at the strategic long-term level of planning. By contrast risk maturation can be most effective when considered in day-to-day business operations. This is sometimes called operationalizing one's approach to risk management and maturation. Operationalizing risk management asks us to take the life cycle models about systems, software and data and connect or pivot them around business operations. We'll take on the view of the workers who use the business logic and the systems or the people who oversee the robotics and internet of things on the factory or warehouse floor and see how each of the different security disciplines brings something to them. This course has five modules. Module one focuses on change management and reveals how this detailed administratively intense process plays a primary role in protecting information systems. We'll also look at its vital contributions to incident response and remediation. Module two shows how physical security design principles are used to monitor and control the flow of physical objects in and out of various security zones. This module also considers the operational effects of safety planning and preparation on people and property, as well as availability and integrity of systems and information. Module three provides a different attitude and mindset about empowering and enabling the people in the organization to become more effective contributors and proponents of its information security. Security training programs have failed to help people complete their job safely and securely. New concepts such as micro chaining demonstrates that security education and awareness can add value to the security process. Module four shows us that system security assessment should be an ongoing task. Security has always involved continuous vigilance and integrity. Formal and informal audits demonstrate just how effective an organization's security controls are. As its process of maturing those controls continues to improve their performance. Module five brings many of these ideas and concepts together through business continuity and disaster recovery planning. The emphasis will be the operational support of these tasks, both in the planning and execution stages. We've prepared the foundations so you can bring concepts covered thus far into a cohesive daily operational context.
Course 8 Learning Objectives
After completing this course, the participant will be able to:
L8.1 - Identify operational aspects of change management.
L8.2 - Summarize physical security considerations.
L8.3 - Design a security education and awareness strategy.
L8.4 - Recognize common security assessment activities.
L8.5 - Classify the components of a business continuity plan and disaster recovery plan.
Course Agenda
Module 1: Participate in Change Management (Domain 1 - Security Operations and Administration)
Module 2: Physical Security Considerations (Domain 1 - Security Operations and Administration)
Module 3: Collaborate in Security Awareness and Training (Domain 1 - Security Operations and Administration)
Module 4: Perform Security Assessment Activities (Domain 3 - Risk Identification, Monitoring and Analysis)
Module 5: Understand and Support the Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP) (Domain 4 - Incident Response and Recovery)
Who Should Take This Course: Beginners
Experience Required: No prior experience required

Information Systems Auditing, Controls and Assurance
The course is awarded The Best Free Online Courses of All Time, and Best Online Courses of the Year (2021 Edition) by Class Central (http://www.classcentral.com).
---
Information systems (IS) are important assets to business organizations and are ubiquitous in our daily lives.
With the latest IS technologies emerging, such as Big Data, FinTech, Virtual Banks, there are more concerns from the public on how organizations maintain systems’ integrity, such as data privacy, information security, the compliance to the government regulations. Management in organizations also need to be assured that systems work the way they expected. IS auditors play a crucial role in handling these issues.
In the course “Information Systems Auditing, Controls and Assurance”, you will explore risks of information systems, and how to mitigate the risks by proper IS Controls. You will also get familiar with the IS Audit procedures and how they are applied during the IS development throughout the Systems Development Life Cycle (SDLC).
Finally, you will get to observe how we can make the system changes more manageable using formal IS Management practices, such as Change Management Controls and Emergency Changes.
The conversations between the course instructor - Prof. Percy Dias, and the IS auditing practitioner will give you a concrete idea on how IS auditors perform their duties, the qualities to become IS auditors and future prospects of IS auditing industry.
This course is suitable for students and graduates from Information Systems, Information Technology and Computer Science, and IT practitioners who are interested to get into the IS auditing field. It is also a good starting point for learners who would like to pursue further studies for IS audit certifications – such as Certified Information Systems Auditor (CISA).

C++ Interacting with the World and Error Handling
Explore the C and C++ languages. Look at the specificity of the C/C++ languages and how this impacts security, ways C/C++ can interact with the external world, error handling, the execution environment and much more.

Basic Cryptography and Programming with Crypto API
In this MOOC, we will learn the basic concepts and principles of crytography, apply basic cryptoanalysis to decrypt messages encrypted with mono-alphabetic substitution cipher, and discuss the strongest encryption technique of the one-time-pad and related quantum key distribution systems. We will also learn the efficient symmetric key cryptography algorithms for encrypting data, discuss the DES and AES standards, study the criteria for selecting AES standard, present the block cipher operating modes and discuss how they can prevent and detect the block swapping attacks, and examine how to defend against replay attacks. We will learn the Diffie-Hellman Symmetric Key Exchange Protocol to generate a symmetric key for two parties to communicate over insecure channel. We will learn the modular arithmetic and the Euler Totient Theorem to appreciate the RSA Asymmetric Crypto Algorithm, and use OpenSSL utility to realize the basic operations of RSA Crypto Algorithm. Armed with these knowledge, we learn how to use PHP Crypto API to write secure programs for encrypting and decrypting documents and for signing and verify documents. We then apply these techniques to enhance the registration process of a web site which ensures the account created is actually requested by the owner of the email account.
How Computers Work
Computers are everywhere, they aren't just the desktops and laptops we use for work but the phones in our pockets and even the watches on our wrists are also computers. You probably use a computer every day and in fact you are reading this on a computer!
Just because we use computers all the time, doesn't mean that we understand them, or find them easy to use. Computer Science is the science of computers, it is the field of knowledge that experts use to understand computer systems. Knowing a little computer science will help you understand the computers all around you.
This isn't a how-to course for a particular piece of software, instead you will learn some fundamental concepts that you can apply to any software or computer system. You'll apply these concepts to the kind of computer systems we use every day, including word processing applications, e-commerce, the internet and web sites. You will learn how to apply computer science concepts to solve problems in daily computer use and generally be a better computer user.
Taking this course could be the start of your career in computer science, and the course is an introduction to the Bachelors in Computer Science from University of London, but it is also for you if you just want to learn a little computer science to help you better understand the computers you use in your ordinary life.

Proactive Computer Security
I’ve heard this before – “I’m not sure my computer security practices are working”. I reply “Have you tested them?” This course is the fourth and final course in the Practical Computer Security specialization. In this course, you’ll learn how to proactively test what you have put in place to protect your data. In the first week you’ll be able to discuss the basics of deterrents and how to “trick” attackers into believing they’ve hit a goldmine of data away from your real systems. In week 2, you’ll be able to understand and discuss the steps of penetration testing methodology. In week 3, you will be able to understand and apply what you have learned on your own systems to test whether your systems are secure or not. In week 4, we’ll discuss planning for your own methodology that you can apply to your own systems. And finally in week 5, we’ll finish up with a project that will allow you to test your skills in a safe environment.

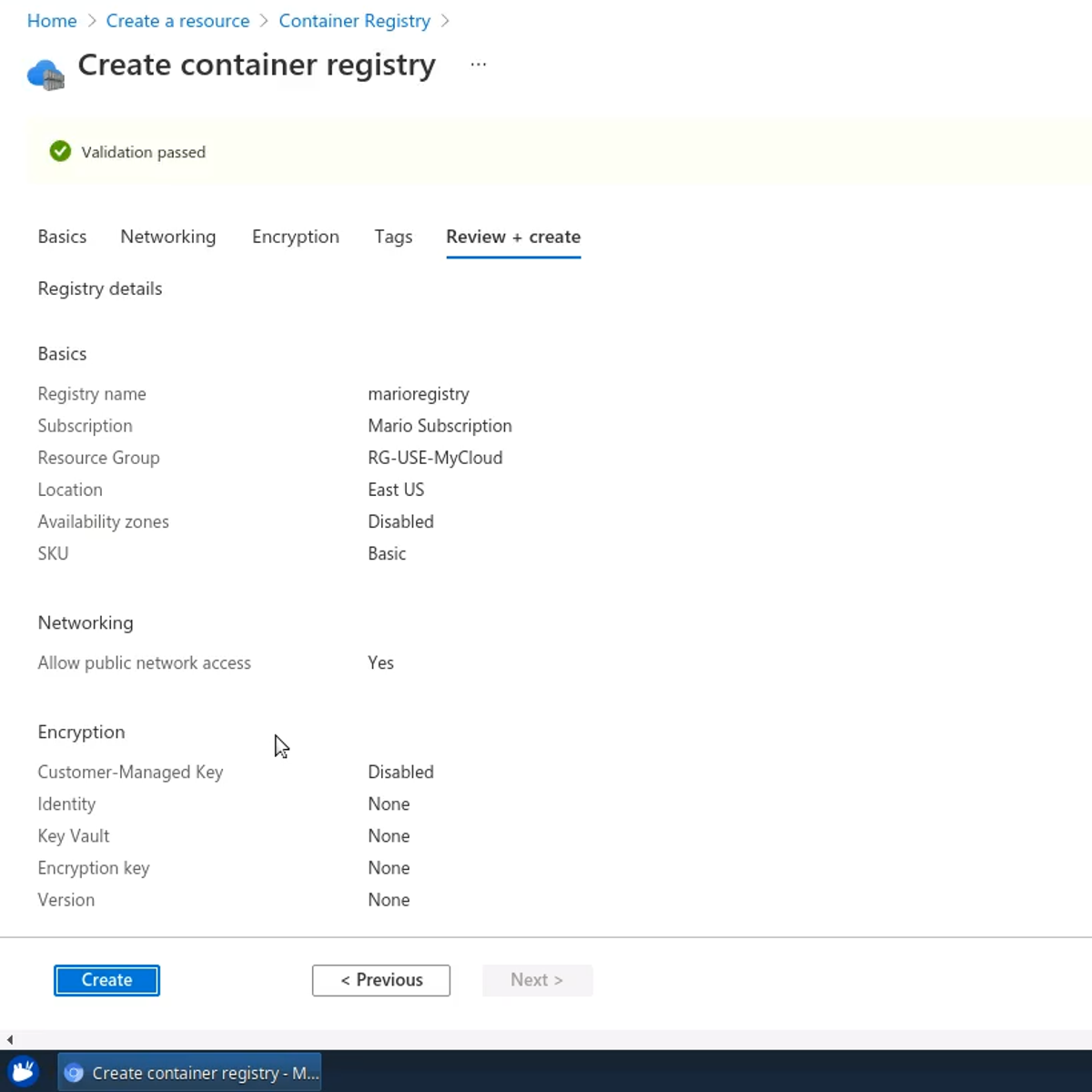
Azure: deploy a Web Server using the Container Registry
In this Guided Project, you will familiarize yourself with the Azure Container Registry, by creating a custom Container Registry to push and pull your own Docker images. You will build images and then run and publish a static web server and a Nextcloud instance, by using Azure Container Instances. You'll learn the basics of the Azure Command Line interface and you will learn how to build an image completely on the cloud.
Note: before taking this Guided Project, if you don't have an Azure subscription yet, please create an Azure Free Trial beforehand at https://portal.azure.com
Popular Internships and Jobs by Categories
Find Jobs & Internships
Browse
© 2024 BoostGrad | All rights reserved