Back to Courses






Computer Security And Networks Courses - Page 20
Showing results 191-200 of 277

Access Control Concepts
Welcome to course 3 of 5 of this Specialization, Access Control Concepts.
In Course 1, we introduced access control concepts. Now, we will take a more detailed look at the types of access control that every information security professional should be familiar with. We will discuss both physical and logical controls and how they are combined to strengthen the overall security of an organization. This is where we describe who gets access to what, why access is necessary, and how that access is managed.
After completing this course, the participant will be able to:
Select access controls that are appropriate in a given scenario.
- Relate access control concepts and processes to given scenarios.
- Compare various physical access controls.
- Describe logical access controls.
- Practice the terminology of access controls and review concepts of access controls.
Agenda
Course Introduction
Module 1: Key Concepts
Module 2: Administrative Controls
Module 3: Physical Controls
Module 4:Logical Controls
Module 5: Controls Review
This training is for IT professionals, career changers, college students, recent college graduates, advanced high school students and recent high school graduates looking to start their path toward cybersecurity leadership by taking the Certified in Cybersecurity entry-level exam.
There are no prerequisites to take the training or the exam. It is recommended that candidates have basic Information Technology (IT) knowledge. No work experience in cybersecurity or formal education diploma/degree is required.

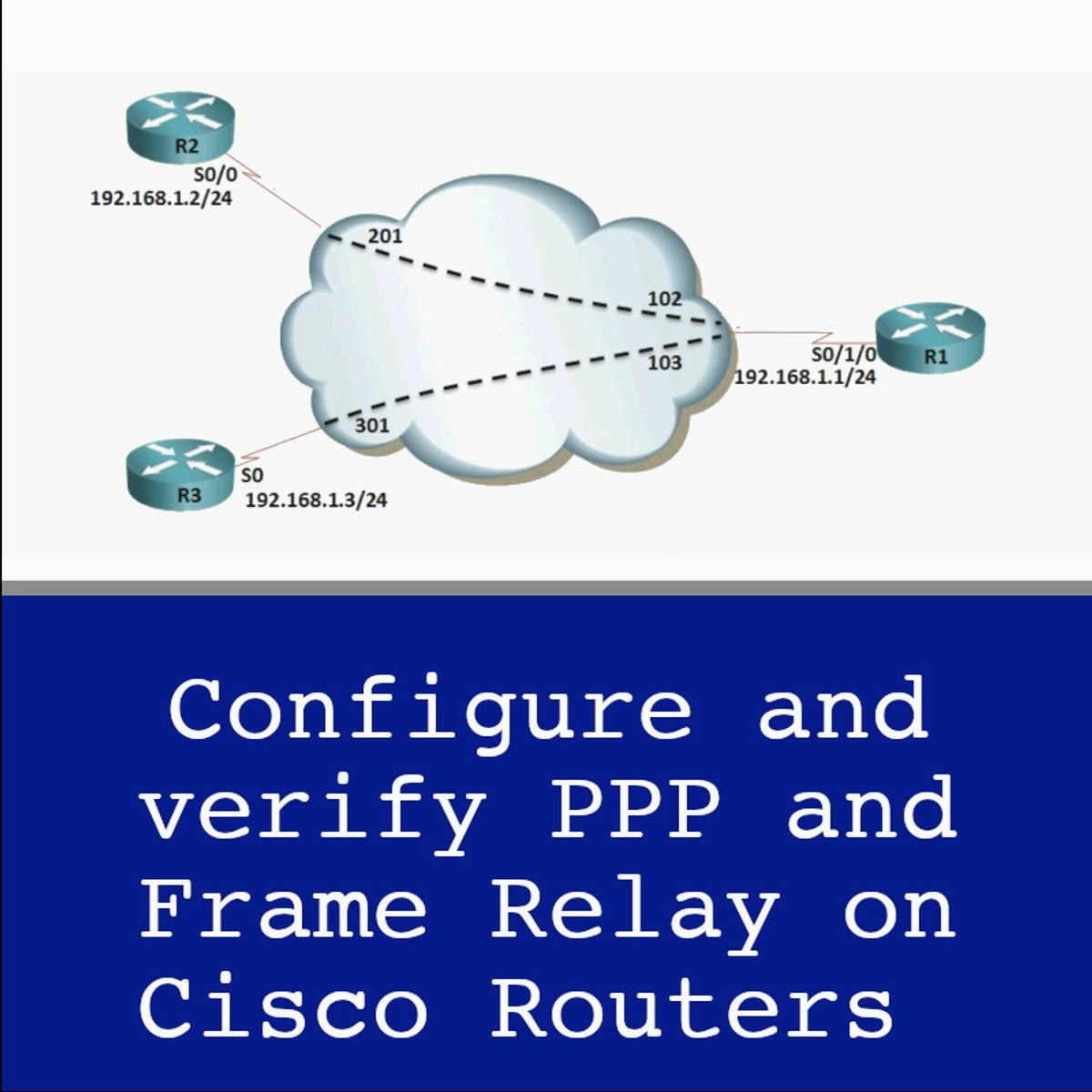
Configure and verify PPP and Frame Relay on Cisco Routers
Welcome to the CCNA 1.10: Configure and Verify PPP and Frame Relay on Cisco Routers, In this guided project, you will configure and verify WAN connections on Cisco routers, you will setup PPP connection and authentication, configure and verify frame-relay, and setup frame-relay sub-interfaces.

Enterprise System Management and Security
The world runs on computers. Your watch, your TV, your car. You might be familiar on how to operate each of these. Your home computer you are even more familiar with operating it. But what does it take to really take computer systems to the next level? - The enterprise level. In this course we discuss what makes home computing systems different from enterprise computing systems. This course will also help you prepare and design your own home lab to explore enterprise operating systems.
This course is for anyone who is exploring what it might take to have a job as a system administrator or for those who are already specialized in one area of system management and would like to move to another. This course may also be for those who are looking to understand how computer security plays an important role in system management.
At the end of the course, you will also be able to illustrate how different enterprise technologies play role in computing at an enterprise level. You will also be able to discuss the three pillars of the CIA triad and how they apply to enterprise systems.
While there is no technical and software component installs necessary for the completion of this course, supplemental how-to guides will be provided if you wish to follow along on the technical portion presented during the course.
Internet History, Technology, and Security
The impact of technology and networks on our lives, culture, and society continues to increase. The very fact that you can take this course from anywhere in the world requires a technological infrastructure that was designed, engineered, and built over the past sixty years. To function in an information-centric world, we need to understand the workings of network technology. This course will open up the Internet and show you how it was created, who created it and how it works. Along the way we will meet many of the innovators who developed the Internet and Web technologies that we use today.
What You Will Learn:
After this course you will not take the Internet and Web for granted. You will be better informed about important technological issues currently facing society. You will realize that the Internet and Web are spaces for innovation and you will get a better understanding of how you might fit into that innovation. If you get excited about the material in this course, it is a great lead-in to taking a course in Web design, Web development, programming, or even network administration. At a minimum, you will be a much wiser network citizen.

CompTIA Practice
This course is geared towards anyone looking to take the CompTIA A+ certification exam. This certification focuses predominately on computer support or helpdesk. This course gives you easy access to the invaluable learning techniques used by many in their preparation of the CompTIA A+ certification exam. This course focuses on two primary areas, visual based questions, and simulation-based questions that are based on common core concepts of the exams. Using these approaches, regardless of your skill levels in the topics and objective areas of the exam, should provide you a glimpse of what a tier 1 helpdesk would be. If you’re already working in the industry or already have experience working as a helpdesk individual for a good length of time, this practice course will cover the more focused details about the exam. If you’re not as experienced, you’ll see not just the focus on exams details, but will also be given the opportunity to explore and grow. If you’ve ever wanted to become certified as a CompTIA A+ technician, this course will help serve as your guide. This course has a wide array of exercises, all with the purpose of ensuring that you have the tools needed to be successful of your exam. The only equipment needed is a computer with internet access.
It is assumed that you have completed the Google CompTIA A+ course.

Technical Deep Dive with Incident Response Tools
The Cyber Incident Response course will give students an understanding of how incidents are responded to at a high level, as well as allow them to build important technical skills through the hands-on labs and projects.
This course starts with a high-level discussion of what happens at each phase of responding to an incident, followed by a technical deep dive into some of the more exciting parts of memory, network, and host analysis and forensics. This course is for anyone wishing to apply learned forensics and offensive knowledge such as ethical hacking to the incident response process.

Decentralized Finance (DeFi) Primitives
DeFi and the Future of Finance is a set of four courses that focus on decentralized finance. The second course is called DeFi Primitives. It is recommended that you take the first course, DeFi Infrastructure, before this course. In this course, we talk about transaction mechanics and introduce both fungible and non-fungible tokens – or NFTs. The course explores the important issue of custody (holding private keys). The course then explores supply adjustment which includes the minting and burning of tokens. The mechanics of bonding curves are introduced. The course then explores the role of direct as well as indirect incentives in the DeFi system. We then analyze swaps or decentralized exchange. We begin by contrasting DEX with centralized exchange (e.g., Coinbase or Binance). The course details the mechanics of Automated Market Makers and provides a number of detailed examples. There is a discussion of impermanent loss as well as (legal) front-running. We end the course by exploring both collateralized and flash loans.

Identifying Security Vulnerabilities
This course will help you build a foundation of some of the fundamental concepts in secure programming. We will learn about the concepts of threat modeling and cryptography and you'll be able to start to create threat models, and think critically about the threat models created by other people. We'll learn the basics of applying cryptography, such as encryption and secure hashing. We'll learn how attackers can exploit application vulnerabilities through the improper handling user-controlled data. We'll gain a fundamental understanding of injection problems in web applications, including the three most common types of injection problems: SQL injection, cross-site scripting, and command injection.
We'll also cover application authentication and session management where authentication is a major component of a secure web application and session management is the other side of the same coin, since the authenticated state of user requests need to be properly handled and run as one session. We'll learn about sensitive data exposure issues and how you can help protect your customer's data. We'll cover how to effectively store password-related information, and not to store the actual plaintext passwords. We'll participate in coding assignment that will help you to better understand the mechanisms for effectively storing password-related information.
Along the way, we’ll discuss ways of watching out for and mitigating these issues and be able have some fun and exploit two different vulnerabilities in a web application that was designed to be vulnerable, called WebGoat.

Capstone Project: Teaching Impacts of Technology
In this project-based course you’ll review the Advanced Placement Computer Science Principles course and exam description guide to prepare for the “Explore Task”, where students must research a recent computing innovation and and analyze its impacts on the world. You’ll also review the description of this task from the student perspective and complete the task yourself. Then you’ll assess sample secondary student work by following the APCSP scoring guidelines as well as provide feedback to a fellow learner on their submitted task and receive the same from fellow learners.
This course is part of a larger Specialization, in which the first five courses focus on teaching impacts of computing concepts and the technology and computing concepts that make them possible, preparing you to teach pre-college learners to be both savvy and effective participants in their digital worlds. While this course and project can be completed without taking the other courses, the bulk of new knowledge is taught there. Additionally, throughout the courses you’ll reflect on your learning experience from both the perspective of the student and the educator, helping you become a more reflective teacher and develop an understanding of how instruction and activities can be designed to support learning.
Note, if your goal is to receive graduate credit from the University of California, San Diego, you need to to make that decision before you complete this course. Please see the FAQ “Will I earn university credit for completing this course?” for details on how to receive that credit.
In terms of CSTA K-12 computer science standards, throughout the Specialization we primarily cover learning objectives within the “impacts of computing” concept, while also including some within the “networks and the Internet” concepts and the “data and analysis” concept. Practices we cover include “fostering and inclusive computing culture”, “recognizing and defining computational problems”, and “communicating about computing”.

VPC Network Peering
This is a self-paced lab that takes place in the Google Cloud console.
Google Cloud Platform (GCP) Virtual Private Cloud (VPC) Network Peering allows private connectivity across two VPC networks regardless of whether or not they belong to the same project or the same organization.
Popular Internships and Jobs by Categories
Find Jobs & Internships
Browse
© 2024 BoostGrad | All rights reserved