Back to Courses








Computer Science Courses - Page 77
Showing results 761-770 of 2309

Object-Oriented C++: Inheritance and Encapsulation
Code and run your first C++ program in minutes without installing anything!
This course is designed for learners with limited coding experience, providing a solid foundation of not just C++, but core Computer Science topics that can be transferred to other languages. The modules in this course cover inheritance, encapsulation, polymorphism, and other object-related topics. Completion of the prior 3 courses in this specialization is recommended.
To allow for a truly hands-on, self-paced learning experience, this course is video-free. Assignments contain short explanations with images and runnable code examples with suggested edits to explore code examples further, building a deeper understanding by doing. You'll benefit from instant feedback from a variety of assessment items along the way, gently progressing from quick understanding checks (multiple choice, fill in the blank, and un-scrambling code blocks) to small, approachable coding exercises that take minutes instead of hours.

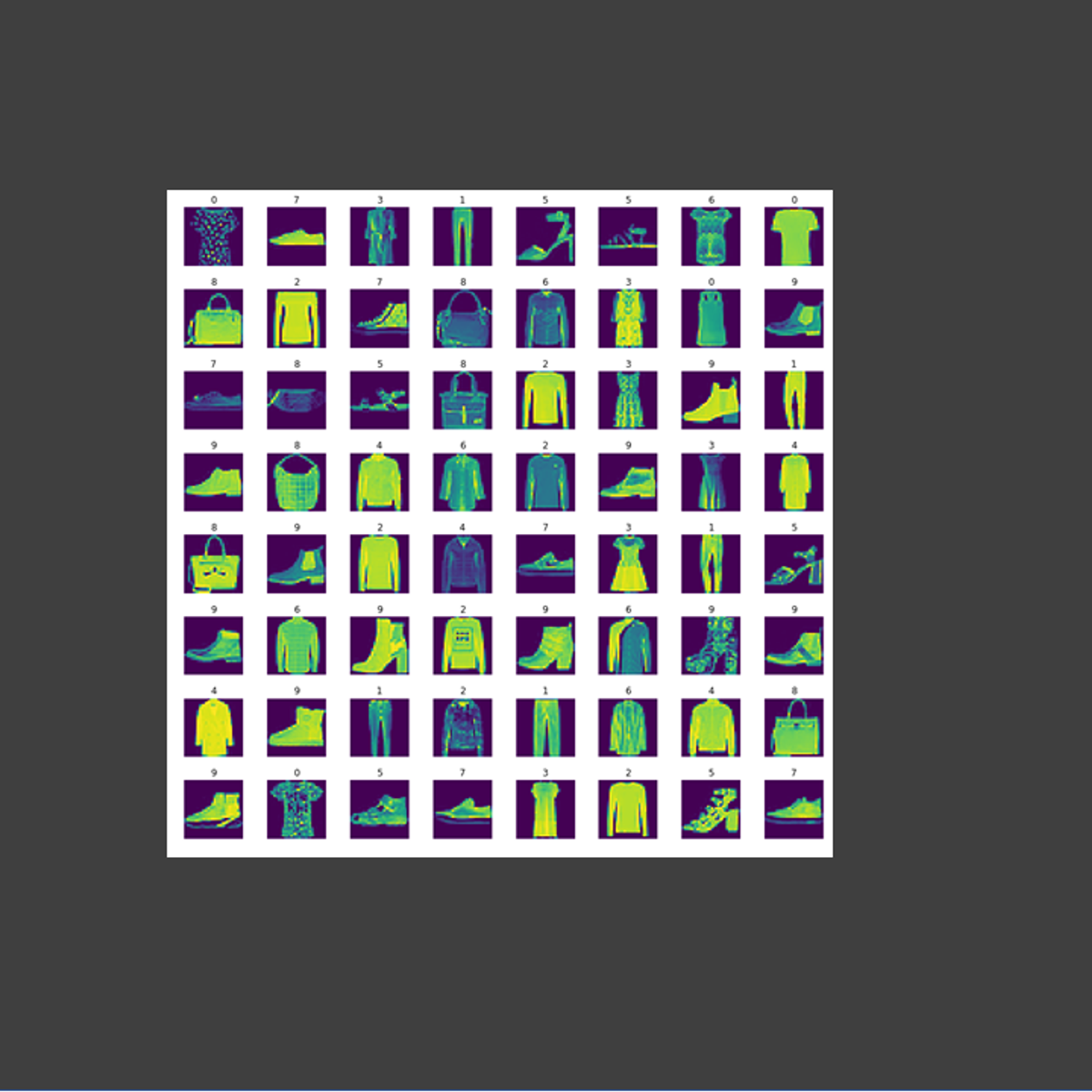
Fashion Classification with Deep Learning for Beginners
Hello everyone and welcome to this hands-on guided project on deep learning 101. The objective of this project is to predict fashion class such as pants, shirts, and shoes from grayscale images. This guided project is practical and directly applicable to the fashion industry. You guys can add this project to your portfolio of projects which is essential for your next job interview.

OWASP Top 10 - Welcome and Risks 1-5
In this course, we will look at the OWASP organization and what its purpose is. We’ll dive into the details of how they create the Top Ten list: where it comes from, how they calculate the severity of each risk and how they determine where each risk ranks. We also review the possible disparity between OWASP’s ranking and your own organization’s ranking, depending on your needs. We will also examine Broken Access Control, Cryptographic Failures, Injection Attacks, Insecure Design and Security Misconfiguration. We’ll use demos, graphics and real-life examples to help you understand the details of each of these risks.

Rent-a-VM to Process Earthquake Data
This is a self-paced lab that takes place in the Google Cloud console.
In this lab you spin up a virtual machine, configure its security, access it remotely, and then carry out the steps of an ingest-transform-and-publish data pipeline manually. This lab is part of a series of labs on processing scientific data.
Input and Interaction
In this course, you will learn relevant fundamentals of human motor performance, perception, and cognition that inform effective interaction design. You will use these models of how people work to design more effective input and interaction techniques. You’ll apply these to both traditional graphic and gestural interfaces.

Unsupervised Algorithms in Machine Learning
One of the most useful areas in machine learning is discovering hidden patterns from unlabeled data. Add the fundamentals of this in-demand skill to your Data Science toolkit. In this course, we will learn selected unsupervised learning methods for dimensionality reduction, clustering, and learning latent features. We will also focus on real-world applications such as recommender systems with hands-on examples of product recommendation algorithms.
Prior coding or scripting knowledge is required. We will be utilizing Python extensively throughout the course. College-level math skills, including Calculus and Linear Algebra, are needed. It is recommended, but not required, to take the first course in the specialization, Introduction to Machine Learning: Supervised Learning.
This course can be taken for academic credit as part of CU Boulder’s Master of Science in Data Science (MS-DS) degree offered on the Coursera platform. The MS-DS is an interdisciplinary degree that brings together faculty from CU Boulder’s departments of Applied Mathematics, Computer Science, Information Science, and others. With performance-based admissions and no application process, the MS-DS is ideal for individuals with a broad range of undergraduate education and/or professional experience in computer science, information science, mathematics, and statistics. Learn more about the MS-DS program at https://www.coursera.org/degrees/master-of-science-data-science-boulder.
Course logo image by Ryan Wallace on Unsplash.

Foundations of Red Hat Cloud-native Development
Foundations of Red Hat Cloud-native Development (DO100a) is designed for IT professionals without previous cloud application deployment experience to learn basic Kubernetes skills. This course is a part of a three-course specialization. In this specialization, you will run, deploy, and test containerized applications with zero-downtime releases.

How to Create a Seamless Pattern Using Adobe Illustrator
By the end of this project, you will be able to create a seamless pattern by using Adobe Illustrator software. Throughout the project, you will be able to create basic shapes and use them in making basic geometrical motifs.
Moreover, we will create a seamless pattern out of these geometrical motifs, and finally, you will be able to change the seamless pattern colors and save your pattern in swatches.
This guided project is for beginner level designers and learners who know how to create basic shapes on illustrator, know the basic tools and commands like creating new file, knowing the shapes tool, eyedropper tool, move & copy commands.
There are a number of reasons why this project is important for artists and designers, it will help you make a seamless pattern out of your designs, seamless patterns are important and mandatory to learn if you want to transform your designs into prints like printing your pattern on fabrics or paper.

Deploy a Web App on GKE with HTTPS Redirect using Lets Encrypt
This is a self-paced lab that takes place in the Google Cloud console.
This lab shows you how to deploy a web app with a browser-trusted TLS certificate. You also deploy an HTTPS redirect on GKE using Let's Encrypt, NGINX Ingress, and Cloud Endpoints.

DevOps on AWS: Operate and Monitor
The third and the final course in the DevOps series will teach how to use AWS Services to control the architecture in order to reach a better operational state. Monitoring and Operation are key aspects for both the release pipeline and production environments, because they provide instruments that help discover what's happening, as well as do modifications and enhancements on infrastructure that is currently running.
This course teaches how to use Amazon CloudWatch for monitoring, as well as Amazon EventBridge and AWS Config for continuous compliance. It also covers Amazon CloudTrail and a little bit of Machine Learning for Monitoring operations!
